Osquery is a tool released by Facebook for end point information collecting and aggregating. Its potential application includes threat hunting, host-based intrusion detection system etc. End point protection/detection is not new. There are lots of enterprise solutions:
- Carbon Black Enterprise Response
- Cisco Advanced Malware Protection for Endpoints
- Confer
- CounterTack
- CrowdStrike Falcon
- Cybereason
- FireEye Endpoint Security (HX Series)
- Guidance Software’s EnCase Endpoint Security
- RSA, The Security Division of EMC, Enterprise Compromise Assessment Tool (ECAT)
- Tanium
- Carbon Black (Windows + Linux)
- Threat Stack (continuous only, Linux only)
Comparing with these solutions, Osquery is cross-platform(Linux, Mac, and Windows) and easy to use. Here are several examples on security investigations:
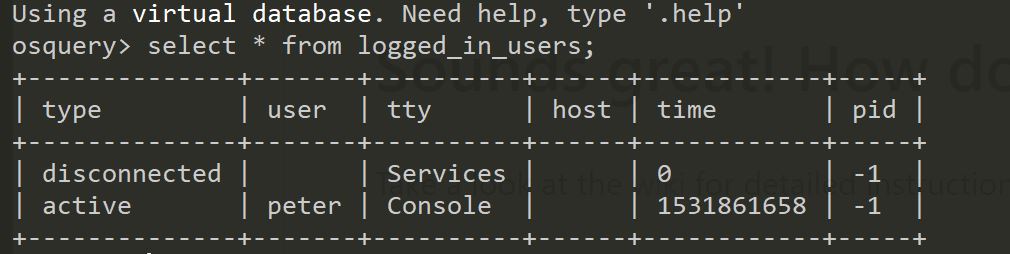
List of all the logged_in users:
select * from logged_in_users;
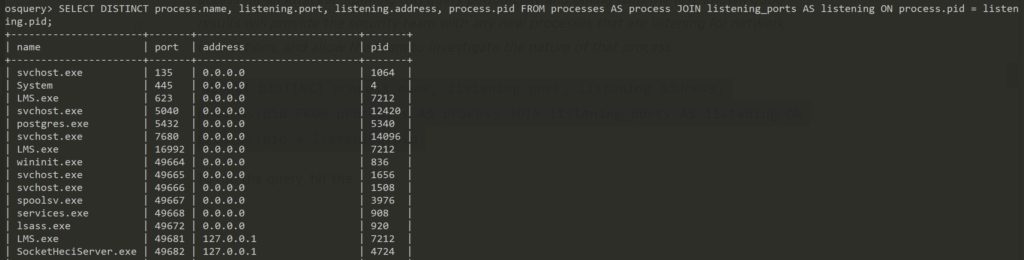
Find new process connections
In command and control attack scenarios, malware could commonly communicate to remote server or inject to other processes to make connections to remote server. In a typical environment, it is very unlikely to see new process to start connecting out. Hence, discovering new process listening on certain ports is very useful in investigation. This is the simple line you can run to find processes that listening on network:
select DISTINCT process.name, listening.port, listening.address, process.pid FROM processes AS process JOIN listening_ports AS listening ON process.id = listening.pid;
Find processes that are running but binary was deleted
select name, path, pid from processes where on_disk = 0;
Find new services that are installed
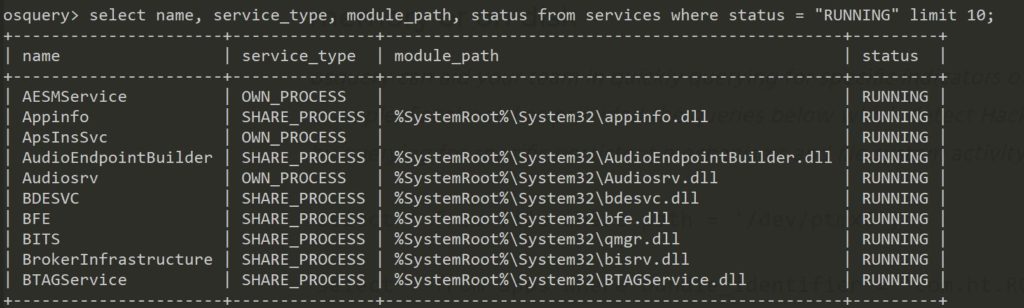
Find specific process of indicators(IOCs) in memory or hard disk. These IOCs could come from any threat intelligence field. This is extremely useful in scope investigation. For example:
select * from processes where name = 'svchost.exe' and path like '%evil%';
In summary, Osquery is powerful. With the help of powerful security data analysis and real-time monitoring, Osquery can be a great tool for security detection and response in the cloud or data center.
When you are ready, here are two things we can help:

