Security Operation Centers (SOCs) receive thousands of security alerts every day. Atomic alerts tend to be very noisy. As noted in a recent white paper provided by Forrester, average security operation team received over 11,000 alerts per day, 53% of the security team’s time is spent triaging and investigation and almost 33% of them are false positives. Alerts that provide little context are very hard to make be actionable. This causes the need for Analysts to spend a large amount of time to investigate alerts to figure out what is going on, where it is happening and why. Other times, because they lack the time to do this analysis, they just choose to ignore those alerts potentially leaving huge risks to go uninvestigated by analysts.
Pattern-driven approach for investigating your security alerts
Alerts are created to represent certain risks. Combining relevant ones provides the necessary context to better evaluate the risk and enables more accurate actions to be taken. Take abnormal logins as an example. It can be a very noisy detection, because the user may use a VPN or just regularly forgot their password. There could, in fact, be hundreds of reasons why the alert can be a false positive. But if you see this alert, alongside the pattern of other alerts, it quickly raises the confidence of even junior security analysts that something bad has likely happened.
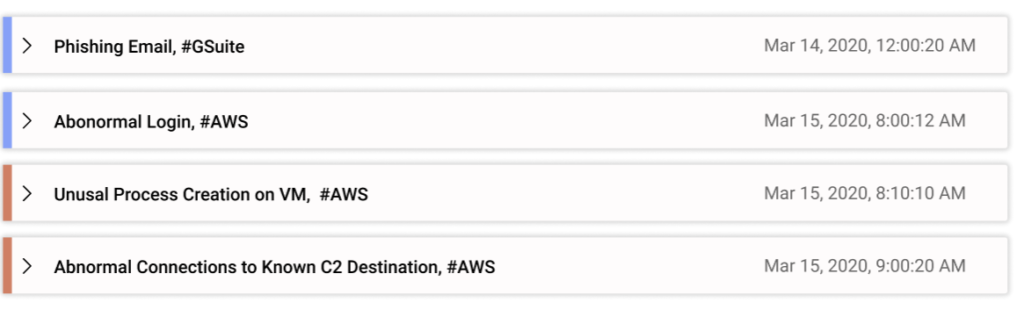
With this pattern-driven approach, true positives can be viewed quickly as being aligned with attack processes such as MITRE ATT&CK framework, as we see above. Likewise, there are patterns for false positives as well. For example, if you see multiple machines connecting to a single IP generating 100 alerts at the same time frame, or always aligning with certain deployment activity, that will give you confidence that they are false positives. As such, these patterns, built to create a context for the alerts, helps to identify both true positive and false positive much faster.
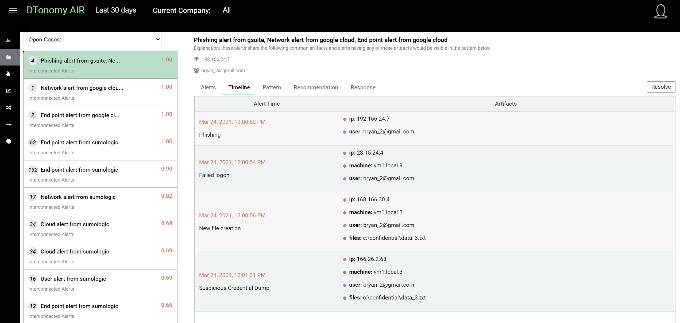
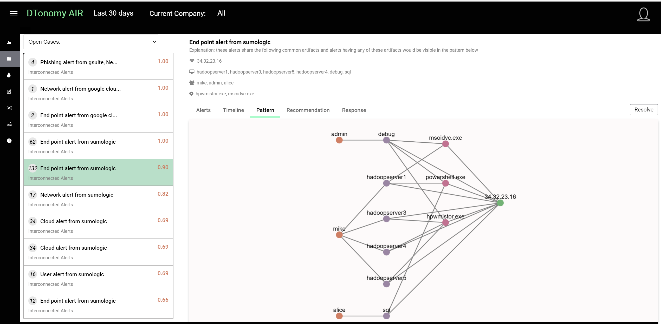
Pattern driven approaches enable you to:
Save time on alerts investigation
Less time on false positive
More context to determine true positives
Together it enables you to reduce risk with less cost.
Augment SIEM with DTonomy’s AIR:
DTonomy augments SIEM by integrating deeply with SIEM system for auto pattern discovery. Our list of SIEM integrations includes but is not limited to:

Learn more about our product here.
Next Blog: let’s align the patterns with MITRE ATT&CK

