Quite often, security teams receive network alerts by their network monitoring systems that someone is scanning ports or there is a possible brute force attack on one or more servers. According to the SANS Institute, port scanning is one of the most popular techniques attackers use to discover services that they can exploit to break into systems. Essentially, hackers send a message to each port on a network, one at a time, to discover and keep track of ports that are open. They can determine not only what services are running, but what services require authentication or allow anonymous logins. A brute force attack is a method of using tools and scripts to rapidly try all combinations of names and passwords in an attempt to gain entry. Logs will show hundreds or even thousands of login attempts over a short period of time. Security teams can create rules in SIEM systems such as Sumologic, Elastic Search, or Wazuh to alert for these types of detections.
How to deal with these types of malicious attacks?
These types of alerts usually start with network detection, yet need extra information and context for further remediation from systems such as endpoint detection and vulnerability scanners.
Incorporating threat intelligence and expert knowledge, DTonomy would recommend the following course of action.
- Block this IP address
- Report the IP address
- Notify others who may be affected to take action as well
- Identify the destination machine and patch any known vulnerabilities
- Investigate Endpoint Detection and Response (EDR) systems to identify any malicious activity on this machine for further investigation and remediation
DTonomy AIR Built-in Playbooks
DTonomy’s AI-Assisted platform provides built-in automated playbooks to assist security analysts in creating comprehensive workflows to address these types of attacks. These playbooks contain integrations to many systems such as:





The playbook that integrates these systems could perform automated response as follows:
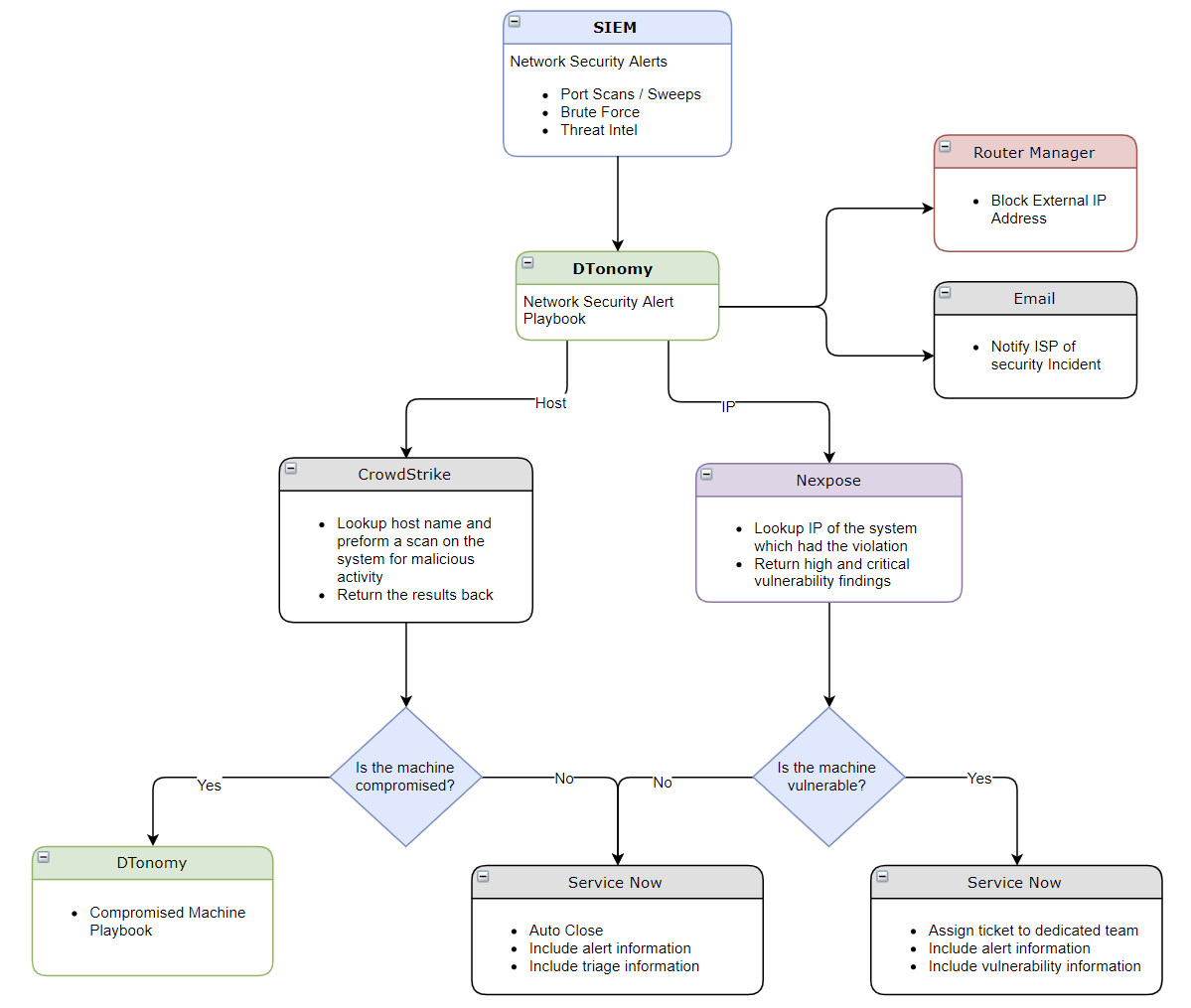
On the left bottom, the workflow is calling other playbooks for a more complete investigation of the target machine and maximizing the usage of similar logic.
More thoughts on responding to these types of attacks:
- It is very likely that the IP you are blocking is a false positive. To minimize the side effect of false positives, you will need to unblock the IPs after a certain time frame (e.g. 24 hours ) if they are not 100% malicious.
- To prevent such attacks, it is a good idea to add CAPTCHA to delay the attackers. Check out the DTonomy service or schedule a call here for a free consultation.
Additional Resources:
More DTonomy Automation Use Cases: Link

