Phishing Investigation playbook
Summary
Phishing investigations can be challenging for a number of reasons. One of the main challenges is that phishing attacks are often highly sophisticated and can be difficult to detect. Phishers may use a variety of tactics to trick people into revealing sensitive information, such as impersonating a legitimate organization or person or using fake websites or email addresses that appear legitimate. This can make it difficult for investigators to identify the source of the attack and gather evidence to support their investigation.
Another challenge in phishing investigations is the need to act quickly. Phishing attacks can be highly time-sensitive, and organizations may need to take immediate action to prevent further damage or loss of information. This can put pressure on investigators to identify and respond to the attack quickly, which can be challenging given the complexity of the problem.
Finally, phishing investigations can be complicated by the fact that they often involve multiple parties and stakeholders, such as the affected organization, law enforcement, and other security agencies. Coordinating the efforts of these different groups and ensuring that all relevant information is shared can be difficult, and can add to the complexity of the investigation.
Overall, the combination of these factors can make phishing investigations difficult and challenging for organizations to manage. It’s important for organizations to have a well-defined and comprehensive approach to phishing investigations, including the use of playbooks and other tools, to help ensure that they can effectively defend against and respond to these attacks.
In order to conduct a thorough phishing investigation, here are 3 playbooks you should follow.
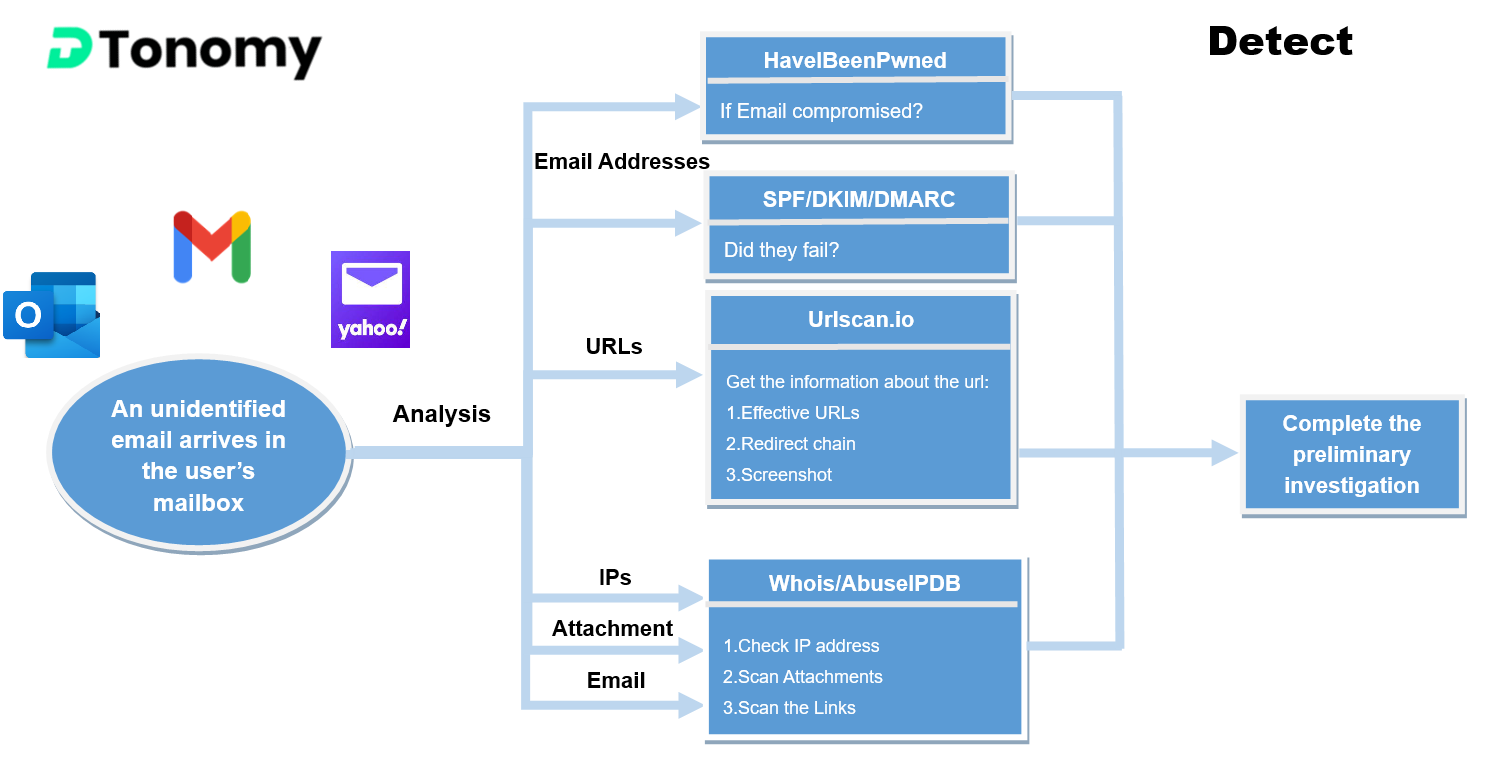
Playbook 1: Detect Phishing
There are several steps you can take to identify whether an email or other communication is a phishing attempt.
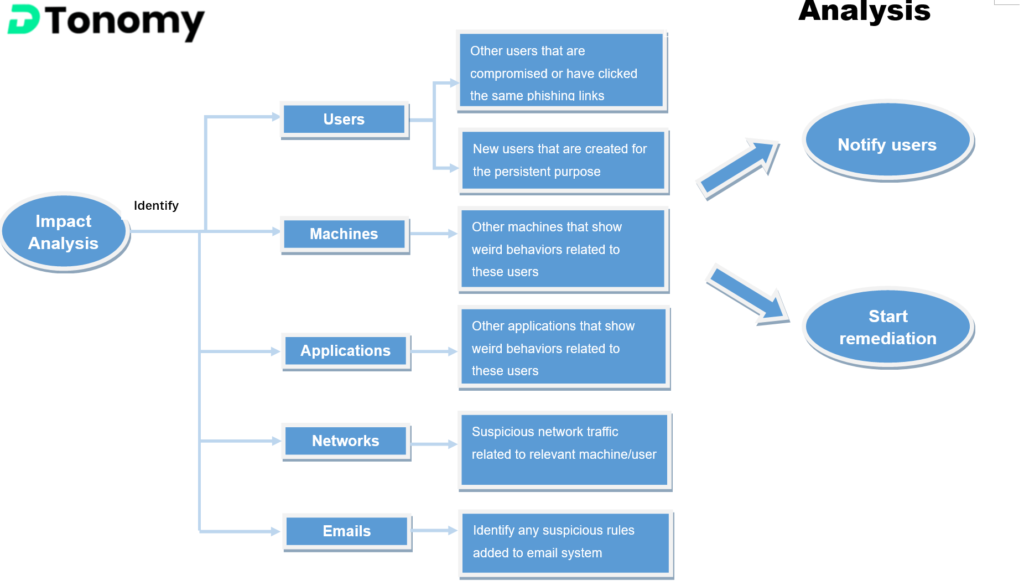
Playbook 2: Impact Analysis
Conducting an impact analysis is an important step in any phishing investigation, as it helps to assess the potential impact of the attack on the organization and its stakeholders. This can include identifying the types of sensitive information that may have been exposed or compromised, assessing the potential damage to the organization’s reputation or financial losses, and determining the need for any corrective or preventive actions.
Impact analysis can also help to prioritize the response to the attack and identify the most critical areas that need to be addressed. For example, if an investigation reveals that a large number of sensitive customer records have been exposed, the organization may need to take immediate action to prevent further damage and notify affected customers. On the other hand, if the attack only resulted in a small amount of information being exposed, the organization may be able to take a more measured approach to the response.
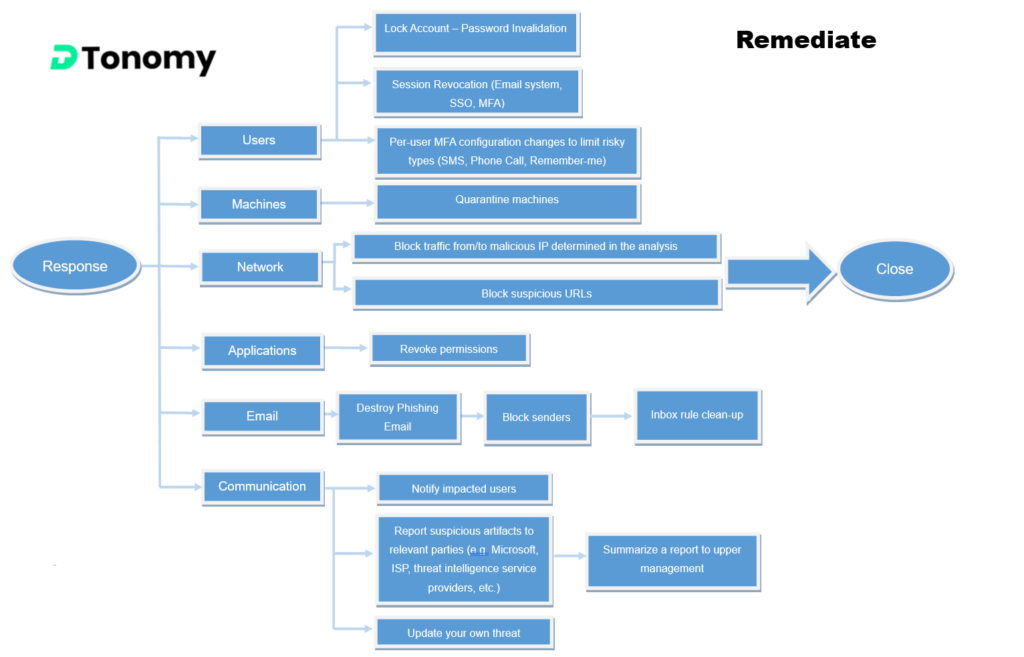
Playbook 3: Phishing Remediation
It’s important to take steps to remediate a phishing attack as soon as it is discovered, in order to minimize the potential harm and prevent further damage. This may involve taking steps such as shutting down the phishing website or email account, disabling any compromised accounts, and implementing additional security measures to prevent similar attacks in the future.
Receiving an excessive amount of reported phishing emails?

Copyright © DTonomy 2024