Hackers are constantly scanning networks and trying to get in via vulnerability exposed via open ports. Therefore, it is important to understand what are the open ports within your network and how to deal with them if there are any open ports. Some ports are required to open for providing service and some are needed to be investigated. As security teams are managing thousands of devices, it becomes only possible to manage these types of risks with automation. Luckily, third-party services such as ShadowServer can assist scan the network on a continuous basis and sending you the report. Once received, a quick way to address these types of risks is to figure out whether there are any new open ports showing up within your network. If new ports showed up, you can reach out to the relevant people for investigation. In this blog, we will show you how to leverage DTonomy’s automation to fulfill this task.
Process:
- Get ShadowServer RDP Scan Reports
- Archive Scan Results to an External Data Storage
- Compare the New Results to the Previous Archived Results
Get ShadowServer RDP Scan Reports
In your workflow, first you need to configure a ShadowServer Report node to retrieve all the RDP open ports’ report IDs as follows:
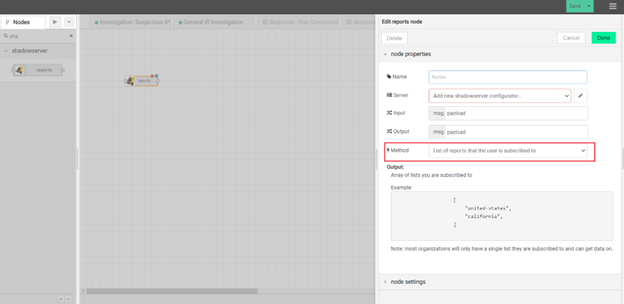
You need to pass input to this node as follows:
{“reports”: [ “united-states”, “california” ],
“type”: “scan_rdp”,
“limit”: 2
}
“reports” are the list of report types you have access to, which you should change according to your own situations.
“type” is “scan_rdp” for this topic.
“limit” is the number of most recent reports you wanna download
The returned results will be a list of entries such as:
{“id”: “-ftVDslHX_hl4grdml_p859FZvc?MerpjjUB9YIgDihWYLpXTw”,
“type”: “scan_rdp”,
“file”: “2022-05-21-scan_rdp-california_system-asn.csv”,
“timestamp”: “2022-05-21”,
“report”: [ “united-states”, “california” ]
}
From this entry, you’ll get the specific report IDs that you’ll need to download corresponding detailed reports.
Still use the same ShadowServer Report node, but configure it to get specific report by ID as follows:
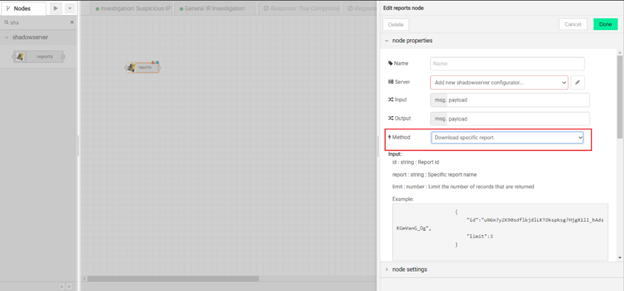
You need to pass input to this node as follows:
{“id”: “-ftVDslHX_hl4grdml_p859FZvc?MerpjjUB9YIgDihWYLpXTw”,
“limit”: 3
}
“id” is the report ID you retrieved from the previous node
“limit” is the number of records that will be returned
From the downloaded detailed report, you’ll get the list of IP addresses that have an RDP port opened for the given date range
Archive Scan Results to an External Data Storage
Suppose you want to archive the results to a permanent data storage, so you can compare the new results with the old results, then find the delta between them.
There’re many options in DTonomy:
- You can save them to a Google spreadsheet using Spreadsheet nodes:

2. You can save them to a file in local file storage
3. You can save them to a SQL Database
Compare the New Results to the Previous Archived Results
Now you have the new result and old result, you want to calculate the delta between them, thus finding out what’re the newly opened RDP ports. You can write your own logic w/ Function Node, or PythonFunction node. Or better yet, you can use the built-in Jsdiff Node as follows:
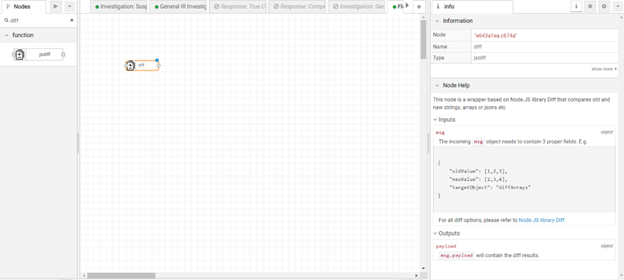
In this case, you want to calculate the diff between an array of old IP addresses and an array of new IP addresses. Thus you only need to set msg.targetObject to “diffArrays”, and set msg.oldValue & msg.newValue to corresponding old & new IP addresses.
Summary
By now, you have an automated workflow that continuously monitors your open ports, especially the changes of open ports in your network so that we can route investigation requests to the team at right time.

