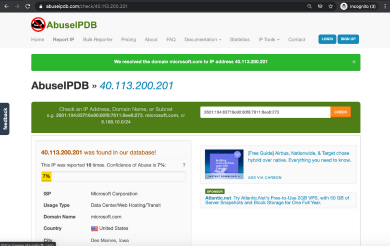
Phishing is an extremely popular type of cybercrime which is used to obtain sensitive information such as usernames, passwords, and credit card details. 70% to 90% of malicious data breaches are due to social engineering and phishing attacks. As employees are more aware of phishing attacks, they are reporting hundreds and thousands of potential phishing attacks to security analyst for further investigation. Here are 7 free tools that will assist in your phishing investigation and to avoid further compromise to your systems.
If you’re interested in delving deeper into the phishing investigation process and tools, we invite you to join our vibrant Slack channel(link) for additional insights.
1. VirusTotal
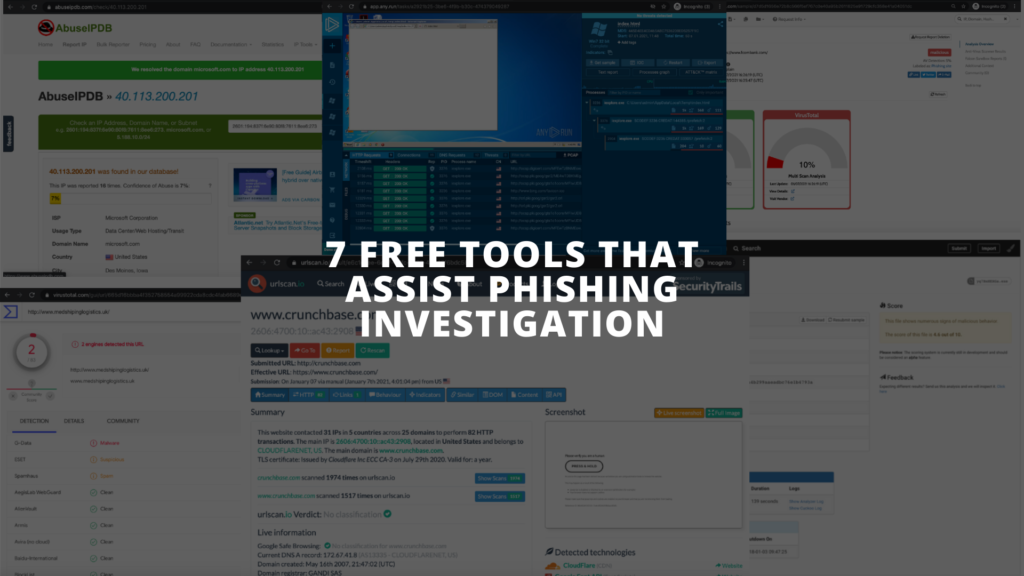
VirusTotal is an online service that analyzes suspicious files and URLs to detect types of malware and malicious content using antivirus engines and website scanners. VirusTotal is a great tool to use to check for viruses that a user’s own antivirus software may have missed and also to verify against any false positives. VirusTotal is free to end users for non-commercial use. They act as an aggregator of information and allow their contributors to share their submission with the security community, allowing VirusTotal to offer an objective and unbiased service to users.

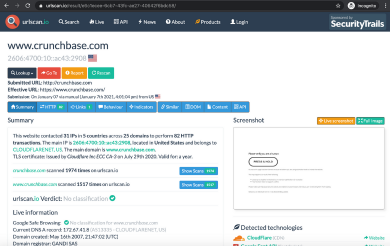
2. urlscan.io
Urlscan.io is a free service to scan and analyze websites. When a URL is submitted, the platform scans the website and retrieves all relevant information. URL scan analyzes programming technologies like HTML, CSS, JavaScript, and/or images. It also looks at cookies, DOM content, server IPs, Domain register, and more. Urlscan.io packages up all the information and delivers it to users along with a screenshot of the website and a verdict on whether or not it is malicious.
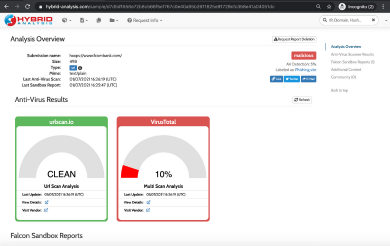
3. Hybrid Analysis
Hybrid Analysis is a free malware analysis service for the security community that enables users to submit files for in-depth static and dynamic analysis. All data extracted from the Hybrid Analysis engine is received as a malware analysis report.
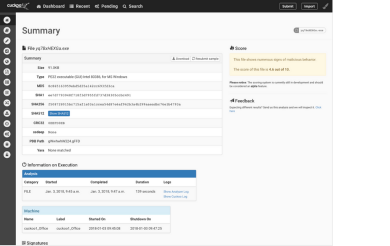
5. Cuckoo Sandbox
Cuckoo Sandbox is the leading open-source automated malware analysis system. The system allows users to upload any suspicious file and in a matter of seconds, Cuckoo will provide detailed results outlining what the file did when executed inside an isolated environment. This allows users to make sure they do not open a potentially malicious attachment.
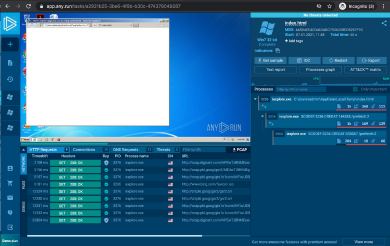
6. Any.Run Sandbox
Any.Run, an interactive malware hunting service enables users to upload and watch the actions of suspicious files without running it on their own systems
7. Open Source SIEM (such as OSSEC)
You need to be able to analyze the login history of this user and correlate other information to identify what are additional potential risk with this phishing email and if there are other abnormal behaviors associated with this account within your system.
Phishing Investigation Playbooks
Navigating through the complexities of phishing investigations can be challenging due to various factors. However, organizations can overcome these challenges by implementing a well-defined and comprehensive approach. Utilizing playbooks and other tools is crucial to effectively defend against and respond to phishing attacks. Here is an example thorough investigation playbook.
AI for Phishing Analysis
Not all suspected emails come with a URL or attachment that is noted as malicious by third-party threat intelligence directly. Therefore you will see phishing emails that look benign by going through all the information above but actually true phishing emails. For example, the following email looks totally legit. The sender is from Paypal and the URLs are legit. It is passing SPF, DKIM, DMARC, etc. However, it is true phishing attackers.
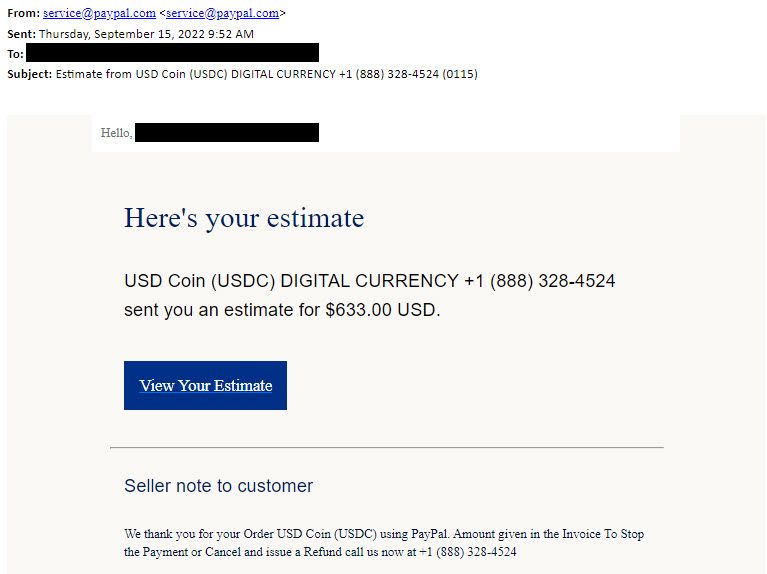
To detect such kinds of phishing, we need extra AI intelligence such as
- Content analysis. What is the tone?
- Behavior analysis. Does this sender send similar things before?
- Image analysis. Without opening the URL on your browser, identify abnormalities on the targeted website based on a screenshot of the targeted website.
This extra intelligence enables you to find phishing emails from stealthy attackers that are hard to detect by traditional methods but becoming more and more popular nowadays.
Unified Tools for Phishing Email Analysis and Response
Every tool provides analysis for a component of email. However, to determine if an email is phishing, you will need a holistic analysis. For example:
- Is URL malicious?
- Is the Attachment malicious?
- Does DMARC/SPF/DKIM Fail?
- Does the sender’s name match sender’s email address?
- Is the sender domain legit?
- Is the email’s sentiment right?
- Does email target your CEO?
- Does the email contain words like invoice, immediately?
- etc.
You will need all the tools to orchestrate with each other to provide comprehensive information/evidence to determine if an email is a phishing email.
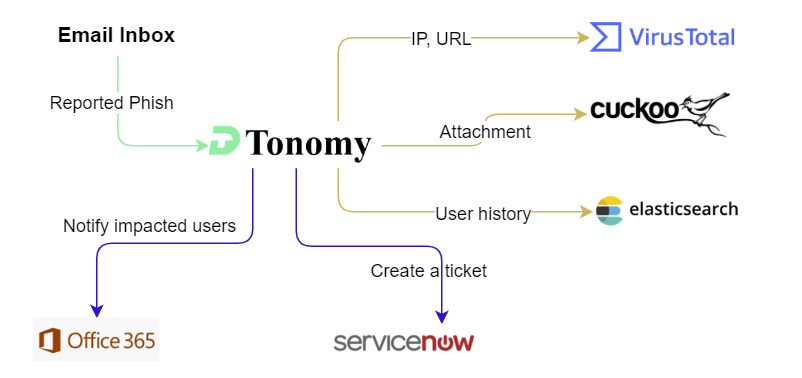
After analysis, you will need to decide what to do with the emails to remediate them completely. For example, here is a list of possible actions you should do in order to cleanly respond to a phishing email.
- Block senders
- Find other users impacted
- Response to reporters with personalized email
- Create a ticket
- Report to ISP or email service provider
- Correlate with other possible attacks within the environment
- Create a report
- Block suspicious URLs
- Block suspicious IPs
- etc.
When you are ready, here are four ways we can help
- Schedule a free consultation to discover the best anti-phishing solutions for you and your team (schedule here)
- Leverage free phishing plugins to analyze your suspected email in outlook and Gmail (Outlook, Gmail)
- DTonomy’s AIR platform enables security teams to automate security analysis and response with AI-based scoring. It takes less than 20 minutes to get everything set up. Get started today! (Sign up here)
- Let DTonomy set up affordable phishing awareness training and manage phishing threats for you by requesting professional service here
If you know your email was compromised
- Reach out to us for immediate assistance at info@dtonomy.com
Additional Resources:
Tips and Techniques for Investigating Suspected Phishing Emails
Prevent Email Spoofing with SPF, DKIM and DMARC
Check out the DTonomy’s Phishing Solutions: DTonomy Phish AIR
DTonomy’s Free Phish Plugin: Outlook, Gmail
Join Slack channel for any questions.