Quantifying and scoring individual security alert are important for security teams to effectively prioritize security tasks. Common scoring mechanisms are the Common Vulnerability Scoring System (CVSS). It is an open framework for communicating the characteristics and severity of software vulnerabilities, owned and managed by FIRST.Org. NIST publishes the Base metrics in the National Vulnerability Database (NVD) with a score ranging from 0 to 10. However, each organization needs to modify the CVSS by their local Temporal and Environmental metrics.
CVSS is a good framework for scoring vulnerabilities, which is part of the security alerts that the SOC team has to process, however it is not suitable for generic security alerts. Security detection vendors like to categorize the severity of security alerts into low, medium, and high based on the credibility of the detections they created. However, most of them are not accurate to each one’s environment. Incorrect scoring for security alerts
- Confuse security analysts
- Affect team morale
- Miss the time window to address important threats
especially valuable for security teams who have already been busy with other tasks.
With proper prioritization, the security team
- Saves time on time tedious investigation
- Automates initial investigation
- Properly allocates resources
- Reduces overall risks
Eight Factors
After working with a few security teams for a while, we’ve summarized a few factors that you need to consider when prioritizing your security alerts:
- External threat intelligence validation
- Does threat intelligence e.g. VirusTotal also find related threats?
- Detection severity score
- How severe is this security detection? (Usually provided by detection vendor)
- Which stage is it in the MITRE framework?
- What is the false positive rate of this type of detection?
- Machine type
- Is it a client-facing machine or an internal machine?
- Who is on the machine?
- Is it a server that stores or access sensitive data or that has some special role in the organization (e.g. domain controller)
- User type
- who is the affected user?
- Is it an account that has privileges (e.g. domain admin, dba)? Is it a VIP?
- Vulnerability on the machine
- Does the machine have a vulnerability?
- How severe is this vulnerability?
- History Intelligence
- Is it the first time to see it?
- Impact
- Is it widespread across a couple of machines?
- Is it targeting one user? A single user that inputs their creds in a fake login page is bad but not as bad as multiple machines getting encrypted at the same time.
- External Defense Intelligence
- Is it being discussed on the internet?
- Is it targeted at my industry?
- Any others in my industry are impacted?
- Did anyone report false positives?
Challenges:
To successfully implement the prioritization for your security alerts, we see there are two challenges
- You need to make sure relevant data are available when calculating
- You need to make sure every factor is properly weighted when combining them
But if implemented, you will see the significant time saving on investigations, proper resource allocations, and faster remediation of important things. Those factors are the things you need to check anyways, why not automate? Automating it will set you up a baseline for accurate prioritization.
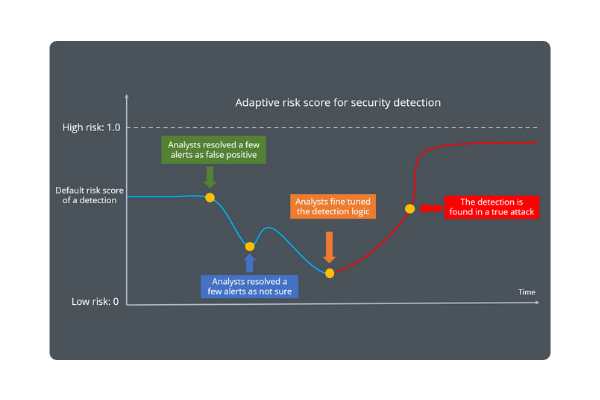
AI-based scoring:
Fixed scoring requires continuous tuning which is time-consuming. The score will drift because it does not update automatically to reflect the changes in your environment. AI-based scoring, which learns from your feedback and learns to distinguish true important alerts from false positives, will continuously learn and update the scores based on the feedback, further saving your time on tuning.
What do you think?
When you are ready, there are two ways we can help
- Schedule a free consultation to help review your prioritization strategy (schedule here)
- DTonomy’s AIR made it super easy to implement prioritization for your organization. You can see aggregated risks immediately once alerts are imported. Get started to manage/prioritize all your security alerts now with DTonomy’s AI-based scoring system DTonomy AIR (Access here)

