Phishing attacks are a common method used by hackers to gain access to sensitive information, and they can be very difficult to detect. By conducting regular phishing tests, organizations can help protect themselves against these attacks by identifying and addressing any vulnerabilities in their employees’ security knowledge and practices.
To run an effective phishing test, there are several key steps you should follow:
1. Identify the goals of your phishing test.
This will help you tailor the test to your specific needs and ensure that you are able to measure its effectiveness. Here are a few common phishing themes
- Gift card redemption
- invoice from a third party
- fake notification of shipment
- Paypal requests
- etc.
Based on your company’s primary business, make sure the relevant phishing themes are fully tested.
2. Choose the right software or service to conduct the test.
There are many options available, so it’s important to research and compare different options to find the one that best fits your needs.
3. Create a realistic phishing email.
The email should be designed to look like a legitimate message from a trusted source, such as a colleague or a known company. It should also contain a link or attachment that will allow you to track who clicks on it.
A popular example is to convert any phishing email you’ve received to simulated phishing with a few changes.
- The first change is to prepare a test account to send simulated phishing
- The second change is to clone a website and host it on a separate server. Once your employees clicked, you can track who clicked and filled in the information.
For example, if you want to use LinkedIn as a phishing site:
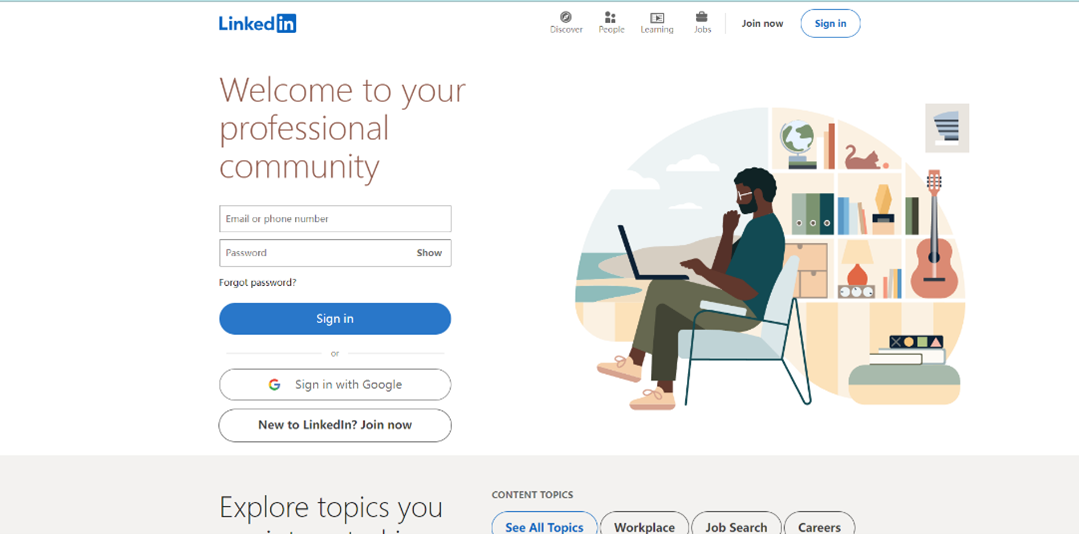
The software can clone the website and make one similar to it.
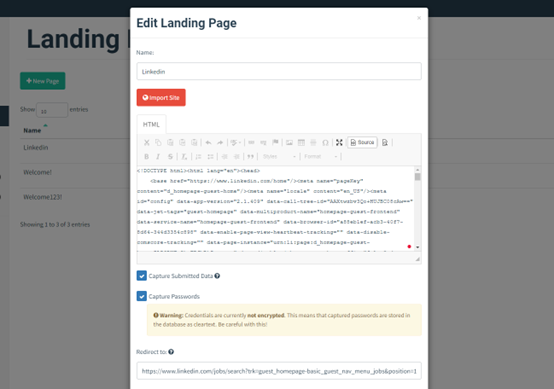
- You will need to figure out where to host the landing page
- In the phishing email, redirect all the phishing links to this new landing page. So that when people click it, they will browse the fake website you set up for them.
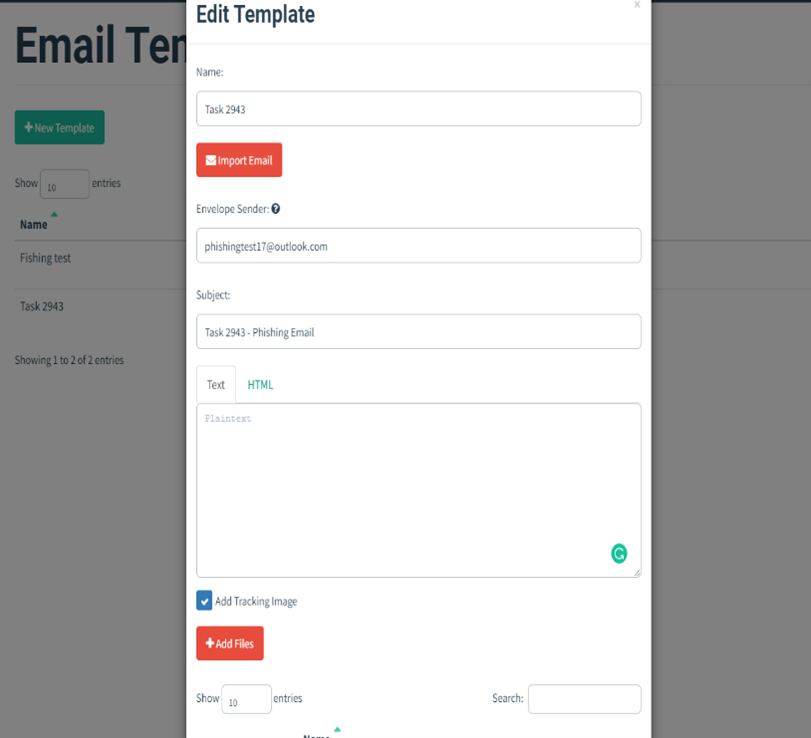
4. Send the email to a selected group of employees.
This group should be representative of the broader organization and should include a mix of different job roles and levels of technical expertise.
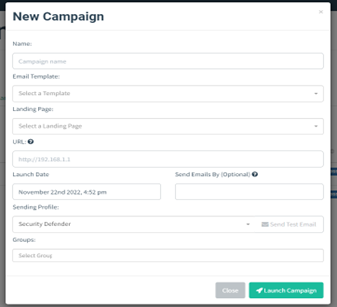
5. Track the results of the test.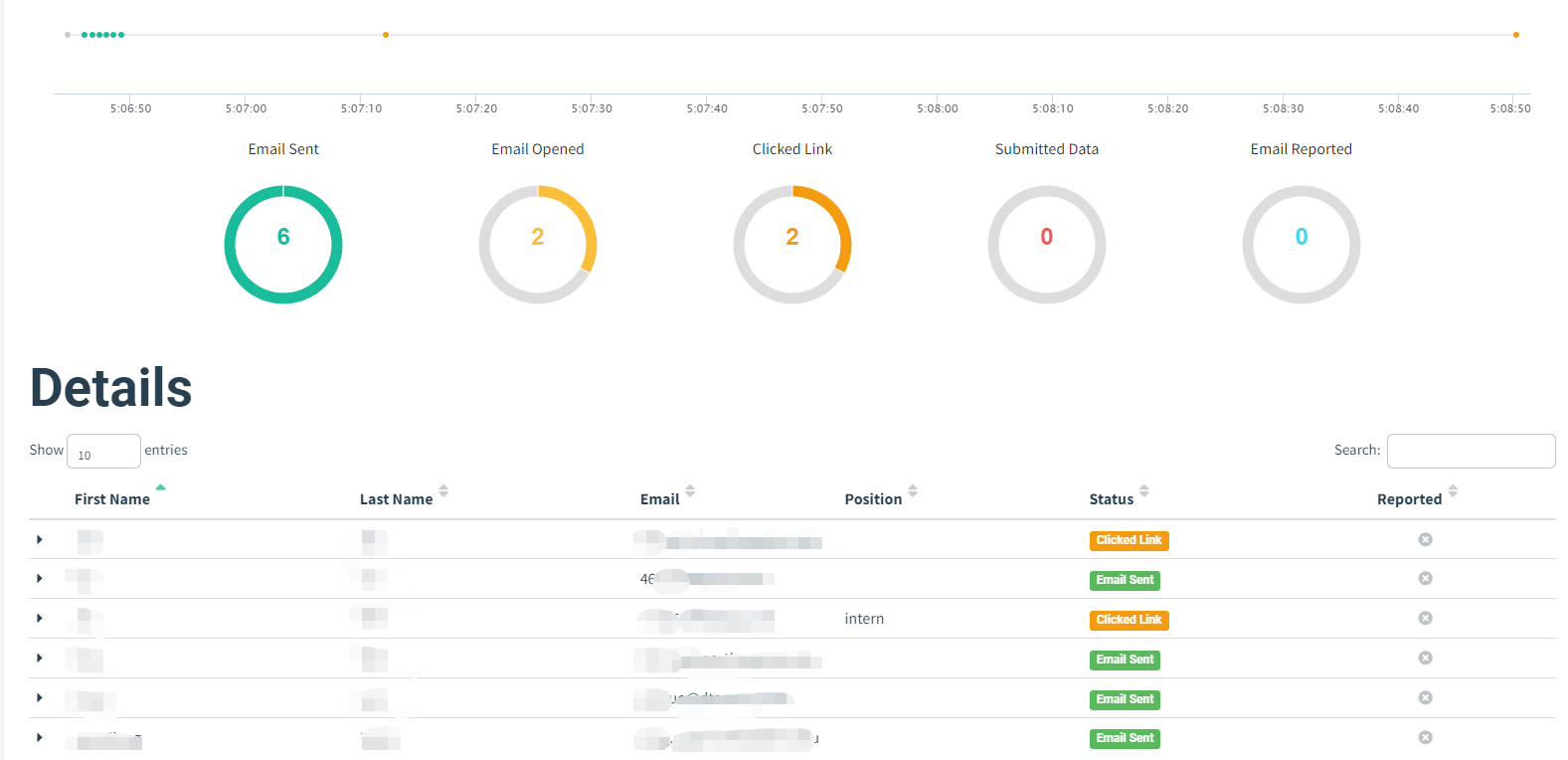
This will typically involve monitoring who clicks on the link or attachment, as well as any other relevant metrics such as the time it takes for employees to report the phishing attempt.
6. Analyze the results and take action.
Once you have collected and analyzed the data from the test, you should use it to identify any areas where your employees are particularly susceptible to phishing attacks and take steps to address those vulnerabilities. This may include providing additional training or implementing new security measures.
By following these steps, you can run an effective phishing test that will help you assess the security of your organization and identify areas where you can improve.
When you are ready, here are three ways we can help
- Schedule a free consultation to discover the best anti-phishing solutions for you and your team (schedule here)
- Leverage free phishing plugins to analyze your suspected email in outlook and Gmail (Outlook, Gmail)
- Let DTonomy set up affordable phishing testing and manage phishing threats for you by requesting professional services (request here)

