A vulnerability scanner enables organizations to monitor their networks, systems, and applications for security vulnerabilities. Most security teams utilize vulnerability scanners to find weaknesses in their environment and make sure preventive actions are taken properly beforehand. The number of vulnerabilities in IT systems is growing fast every day. Over 8,000 vulnerabilities are reported in Q1 of 2022. Popular vulnerability scanners include CrowdStrike falcon spotlight, Rapid 7, Tenable, ShadowServer, Qualys, etc. To make sure vulnerabilities are timely patched, one important part is to make sure they are visible to the parties that are relevant. For example, your management team and your clients. Popular business intelligence tools such as Power BI is a great tool to achieve this. In this post, we outline the process to quickly build up an automation to create a Power BI report on the summary of vulnerabilities based on Crowd Strike Falcon Spotlight vulnerability information.
CrowdStrike Falcon Spotlight
CrowdStrike Falcon Spotlight offers security teams a real-time assessment of vulnerability exposure on their endpoints. It collects endpoint vulnerability data based on a single agent provided by crowd strike.
Power BI
Power BI is a popular business intelligence tool provided by Microsoft. Teams can use Power BI to create and share nice dashboard and report within a team or for clients.
Comparing other dashboard solutions e.g. SIEM, Power BI is
- Very easy to set up and customize
- Professional quality for reports good for management and customers
- Very easy to share
Data Transformation
Before you create a nice report for your customers or share it between teams, you will need to stitch crowd-strike vulnerability information together in the desired format so that you can use it to build the report. The following shows an automated solution that you can reuse to stitch vulnerability data from CrowdStrike Falcon Spotlight to Power BI. It is an out-of-the-box solution and you can reuse it almost immediately.
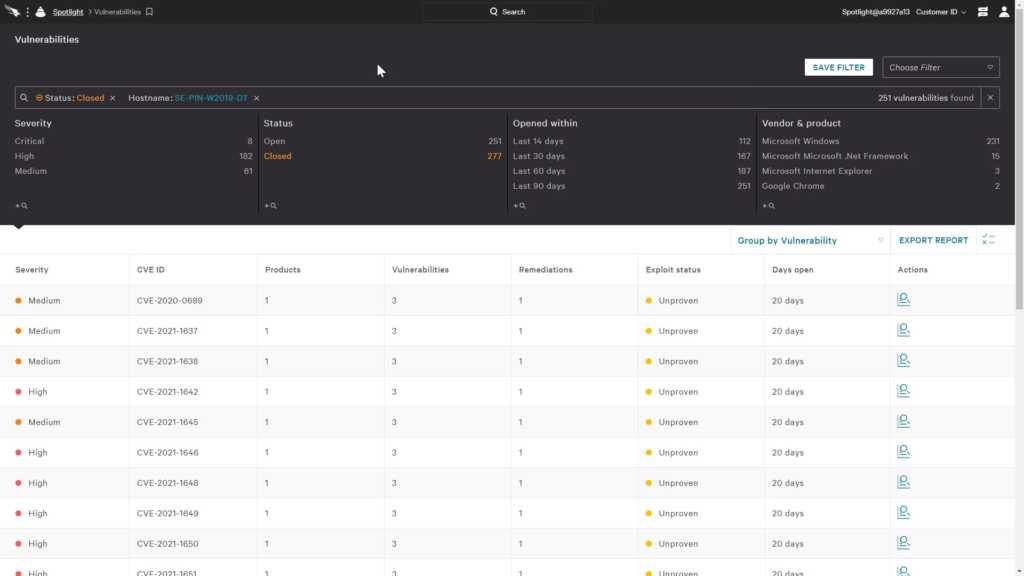
CrowdStrike Falcon Spotlight APIs
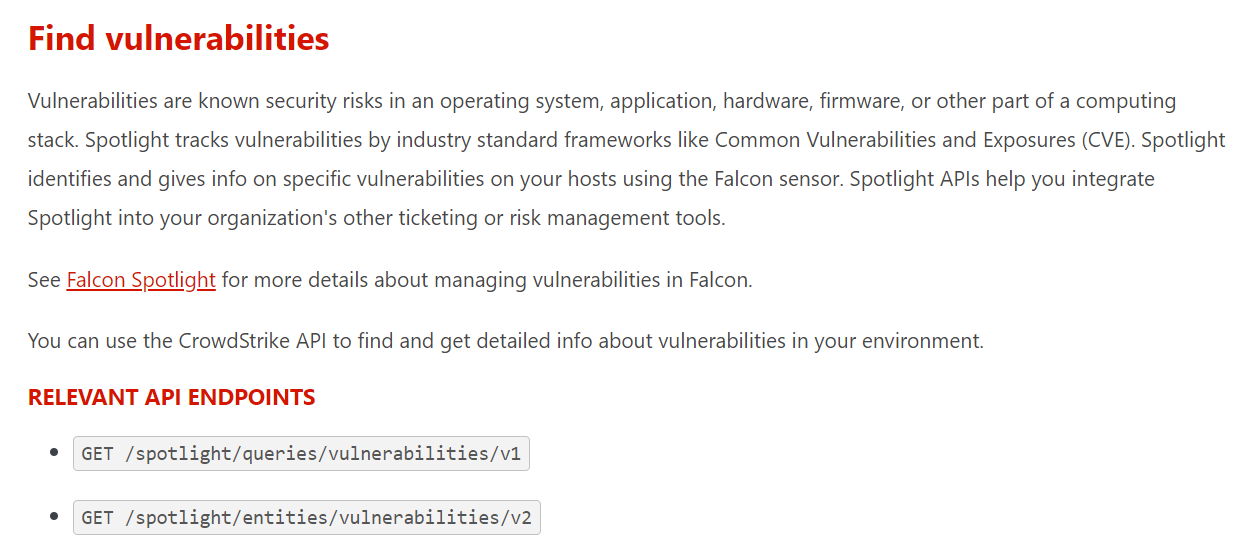
CrowdStrike Falcon Spotlight has two APIs
- Get one or more vulnerability’s ID
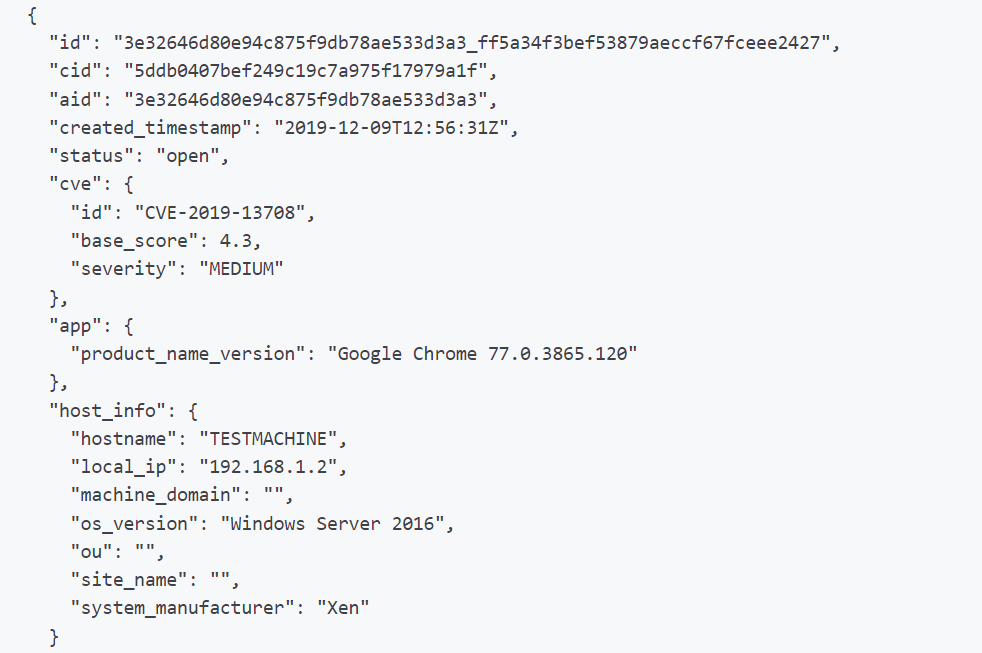
GET /spotlight/queries/vulnerabilities/v1This API returns a list of vulnerability IDs. However, it does not provide vulnerability details. In order to take CrowdStrike details, you will need to use another API to complete the requests.
2. Get vulnerability details
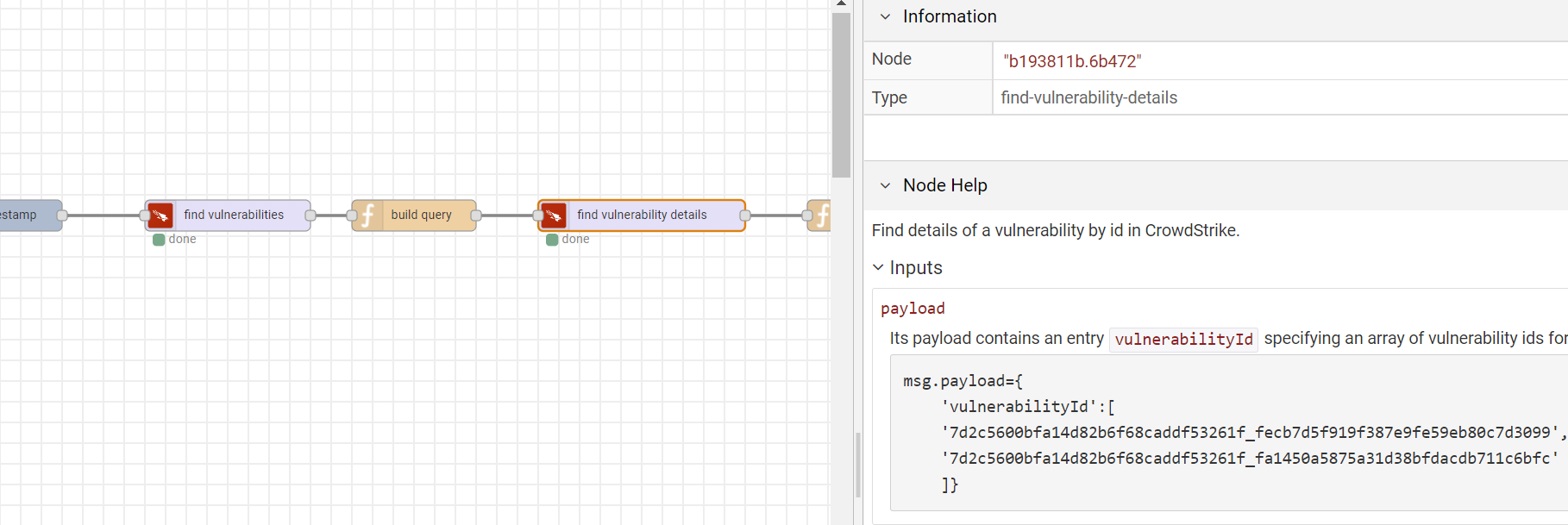
GET /spotlight/entities/vulnerabilities/v2This API returns vulnerability details based on a vulnerability id or a list of vulnerability ids.
Power BI API
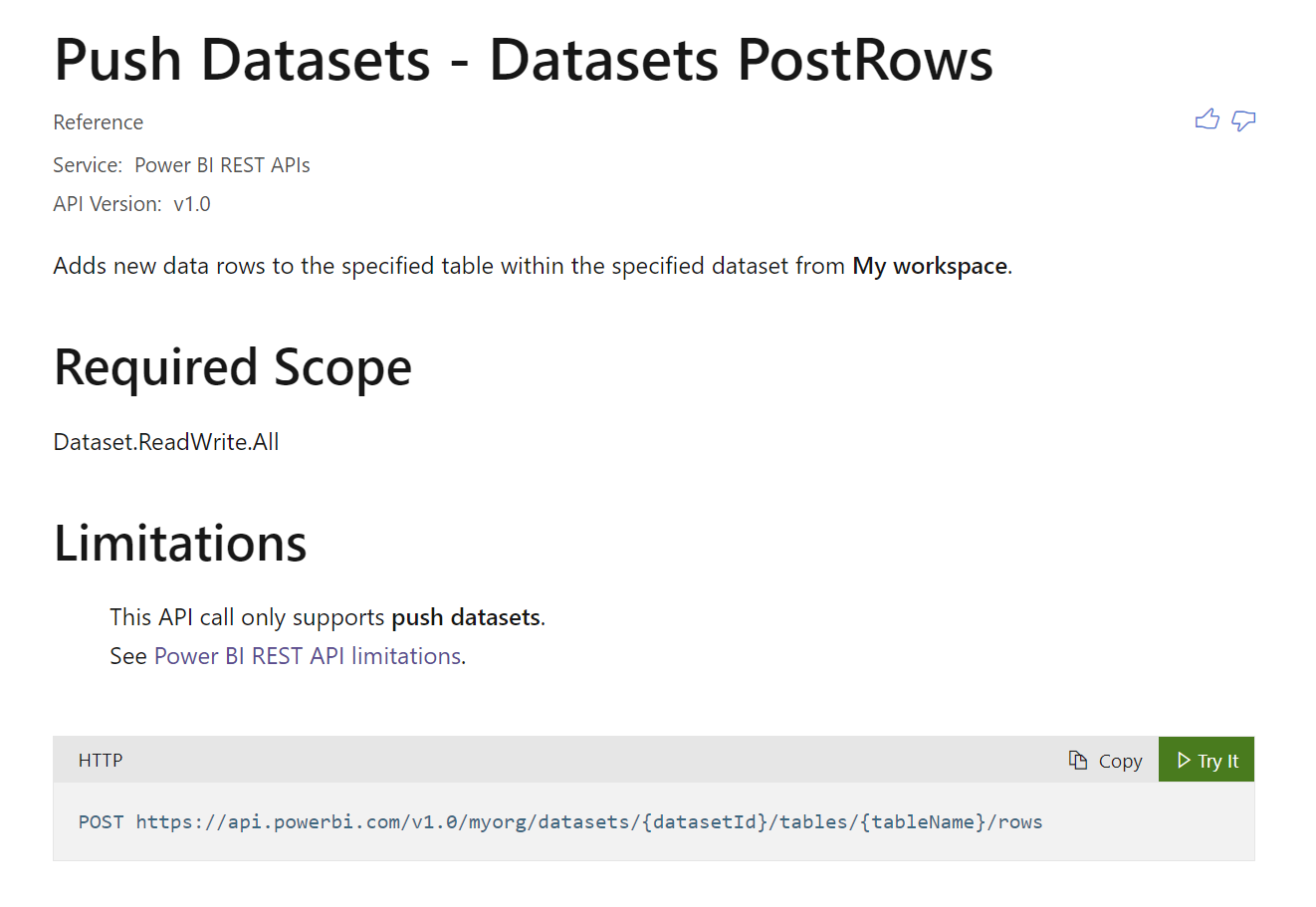
To post rows to Power BI, you will need to use Power BI API to post data row by row.
POST https://api.powerbi.com/v1.0/myorg/datasets/{datasetId}/tables/{tableName}/rows
End-to-end data pipeline automation
The output of CrowdStrike is a JSON Object which contains a list of information. To transform it, you will need to map that to a table schema in Power BI. DTonomy’s end-to-end automation for pulling data from CrowdStrike Falcon Spotlight and stitching them together is here:
Retrieve data from CrowdStrike Falcon:
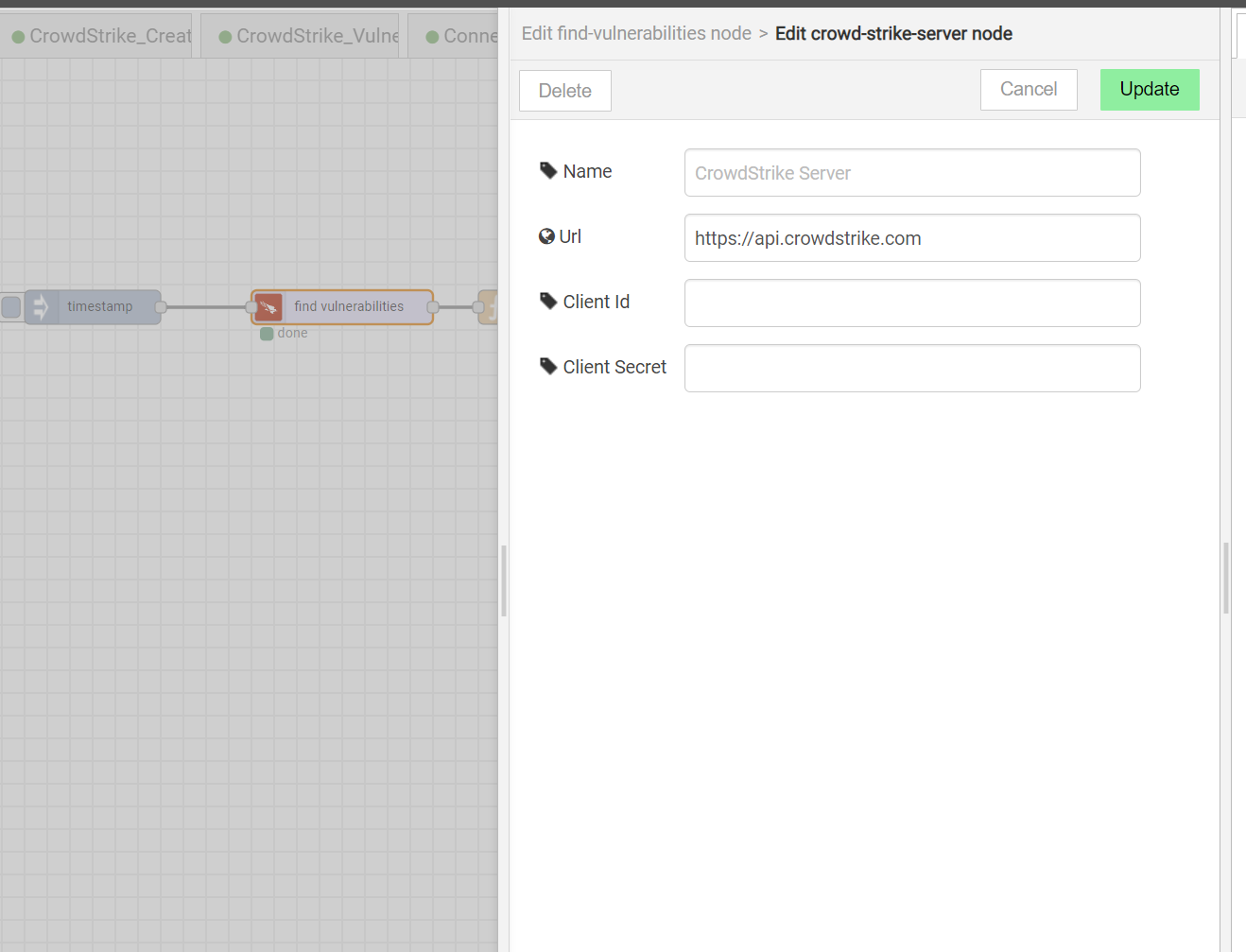
Fill in CrowdStrike Connection Information and then pull vulnerability Ids. The CrowdStrike API Connection Information can be found on CrowdStrike Instance.
Once you have a list of vulnerabilities, let’s retrieve vulnerability details.
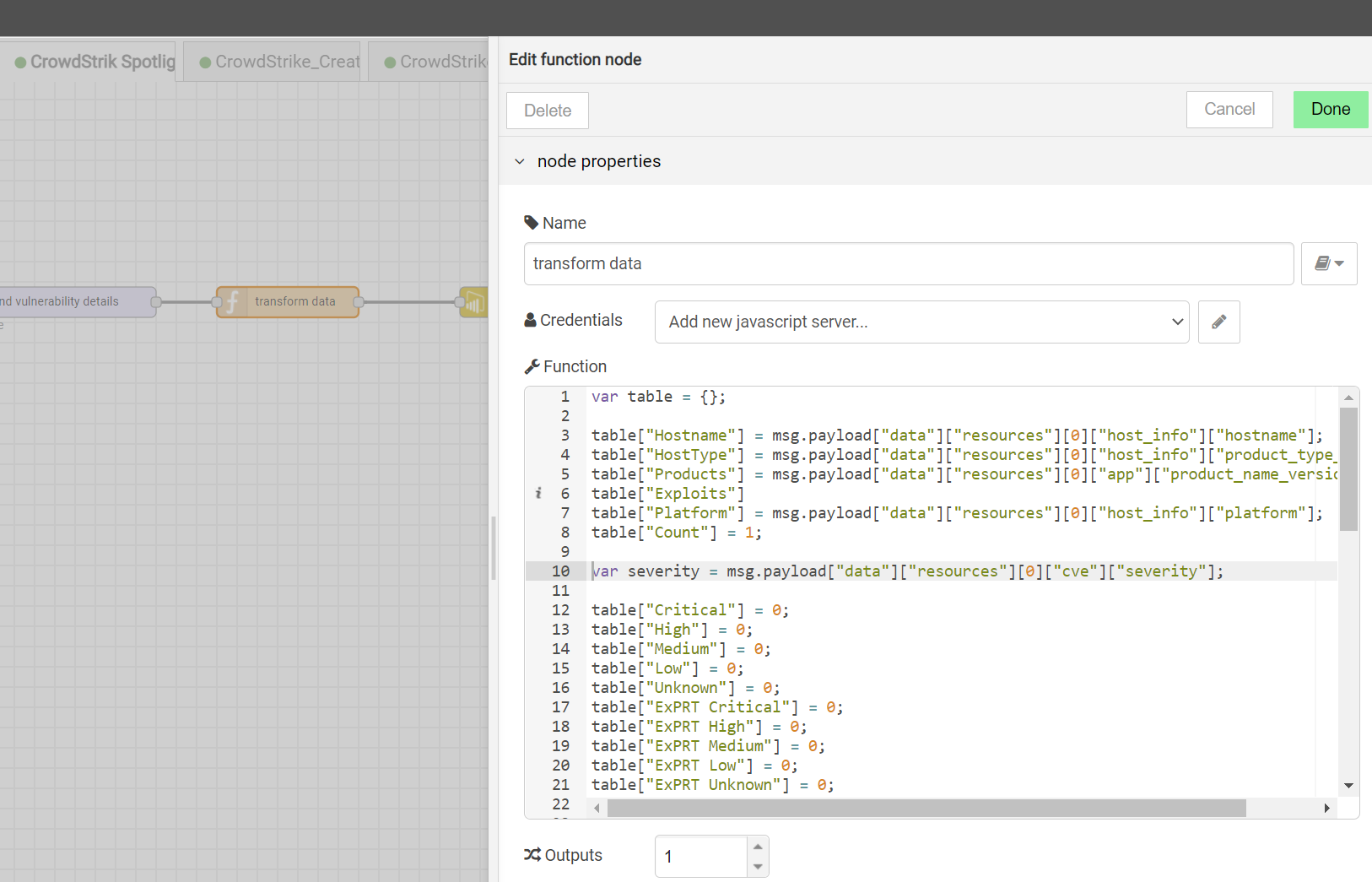
Data Transformation:
The function node in between Vulnerability Details and the Power BI node is the transformation where you can transform data or enrich data or customize data to the format you would like to send
Upload data to Power BI:
Select the post rows to function under datasets operation and also include your desired workspace id and Power BI credentials to upload transformed data to Power BI
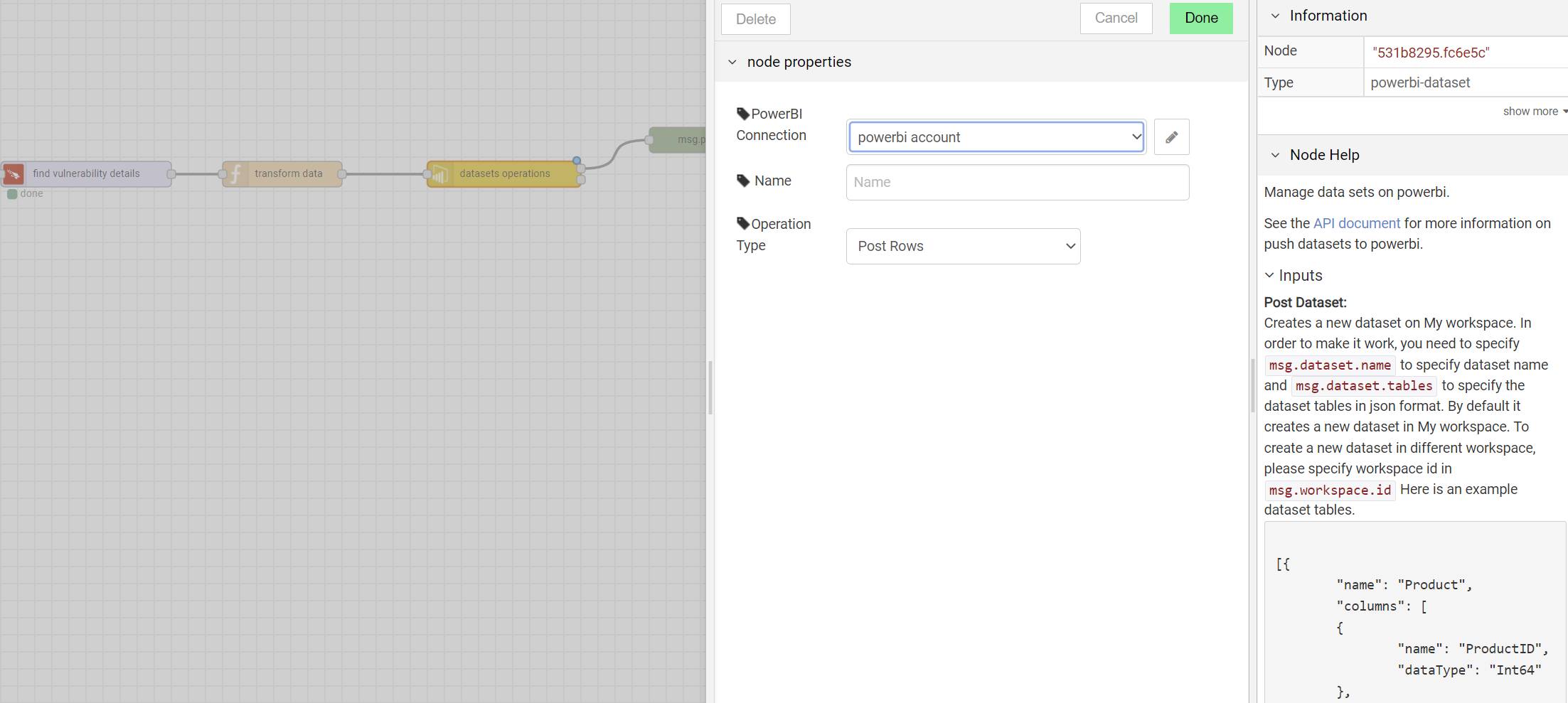
This takes the transformed data and then uploads it to Power BI.
Fully automated workflow
An end-to-end automated data pipeline is like this.
Step 1: pull all vulnerabilities from CrowdStrike Falcon Spotlight
Step 2: based on vulnerability ids, pull vulnerability details
Step 3: transform and select vulnerability information to table format
Step 4: Upload data to Power BI
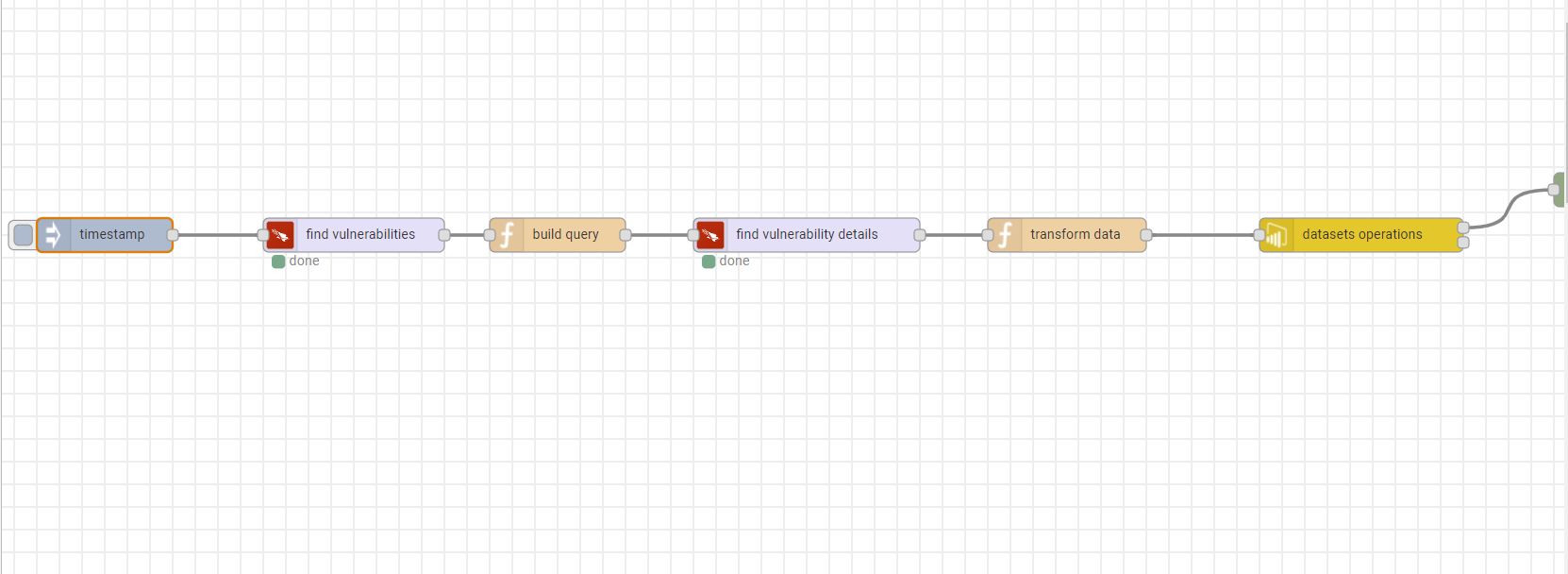
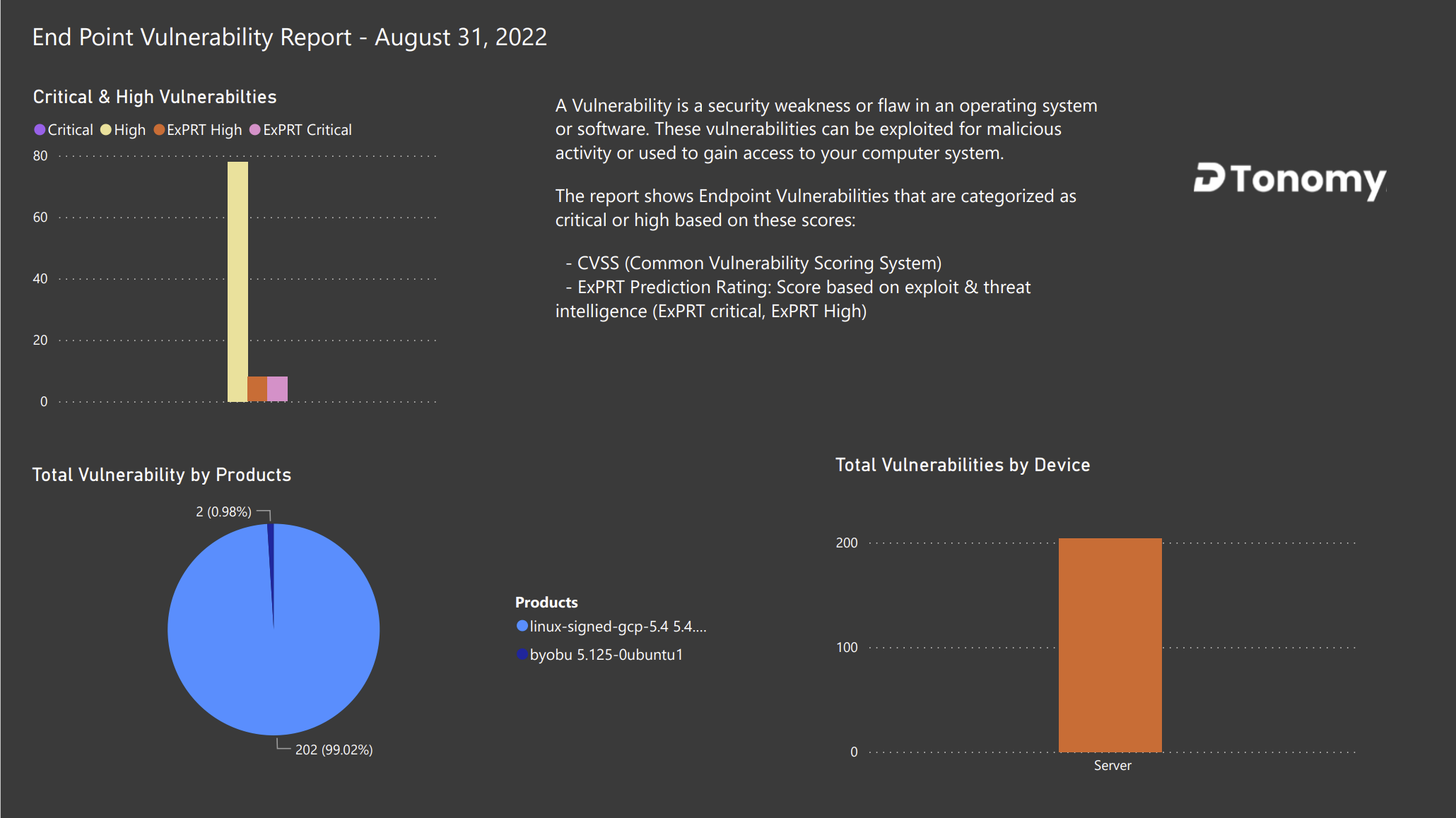
Once automated, you can schedule it to run every day or every week. Based on updated data, you can easily create a nice vulnerability summary report like this.

We provide different types of templates that can be reused for different reports purpose.
Share your report
From Power BI, you can now easily share reports with your client or your other team members.

Aggregated vulnerabilities on multiple different tools
It is very common you may have multiple scanners besides CrowdStike Spotlight, for example, Tenable, Rapid7, etc. With the flexible integrations, now we can easily dedupe the vulnerabilities and provide a unified view on vulnerabilities.
Multi-Tenant Vulnerability Management
Managing CrowdStrike in multi-tenant environments can be challenging and risky when it comes to retrieving vulnerability information. Instead of using a separate API key for each tenant, our solution allows you to easily authorize access using a parent API key and tenant customer id. By doing so, you can generate a token for each tenant and retrieve vulnerability information in a secure and efficient manner.
Look for other integrations?
DTonomy’s platform has 100s integrations with various kinds of security tools. Check it out here. If it is not there, just reach out to us. We are continuously adding more integrations.
With more integrations, you can now aggregate different vulnerability information and security insights and present them in one nice report.
When you are ready, here are two ways we can help
- Check out More examples on Security Dashboard and Reporting
- Schedule a free consultation to discover the best solution for you and your team (schedule here)
Additional Information
- DTonomy’s CrowdStrike Enhancement service is here
- Relevant Blog: Continuous Security Reporting using popular BI tools
- Automate Security Executive Dashboards on Power BI: How to Architect the Data pipeline