New Phishing & Malware Threats are Increasing in the Wake of the Coronavirus
Corporate phishing and malware scams from hackers masquerading as companies reaching out about the COVID-19 epidemic have dramatically increased as the virus continues to spread. These hackers are leveraging the widespread uncertainty by sending employees official looking messages from authority figures within their company. These emails may detail company plans to close locations, begin remote work, and even include tips for keeping the employee and their family safe by using credible information from the World Health Organization (WHO) and Center for Disease Control (CDC) among others.
How These Scams Work
In the legitimate looking email, there will be a request for an immediate action to be taken by the email recipient – either downloading a file or following a link and entering their login credentials.
Downloadable files will typically appear to be a PDF of a critical piece of information like an updated company policy, alert from a health organization, or announcement from an executive. After downloading these files, a variety of malicious software or malware may be installed that can track your keystrokes, access personal and financial information, and even take control over your computer.
Phishing links will appear to be legitimate and often direct you to an official looking password login form from Microsoft, Google, or others. The goal of these types of scams are to obtain your work login credentials so the hackers can access private company documents, emails, customer data, and confidential information. Below is an example of a fraudulent phishing email that could be sent to you:
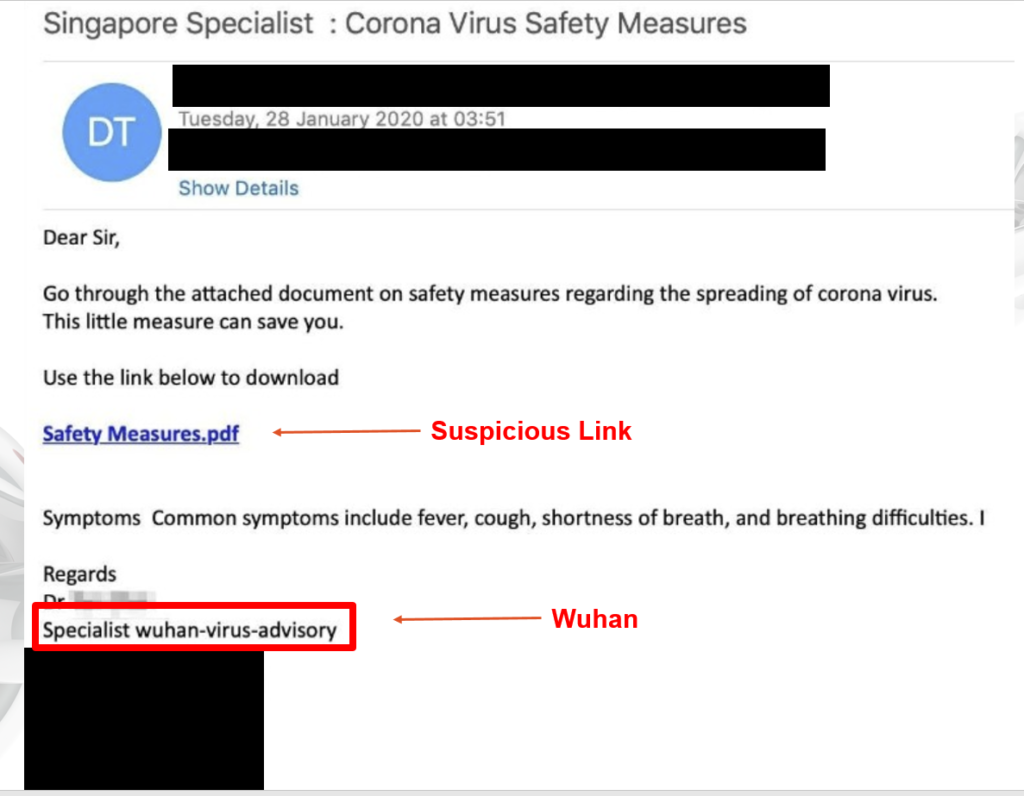
How to Recognize & Avoid Common Phishing & Malware Emails
Like traditional email scams, there are a few distinct ways to determine if the email you were sent is an attempt to steal your login credentials or install malware. Use these tips below to avoid these malicious emails:
- Generic and a-typical greetings: if the greeting at the top is different from similar emails you have received in the past from the sender or it does not use your name (“Dear sir or madam” are examples) this may be an indication the email is not genuine.
- Obvious spelling or grammar errors: When the message or subject includes spelling, punctuation, or grammar errors there is a strong likelihood that you have received a phishing email.
- Urgent requests for personal information: Often times hackers will try and get you to do something immediately whether it’s sending personal information, entering a password, or downloading a file.
- Review the senders email address and links: Make sure to expand the senders information at the top of the email to check if the sender is legitimate, if there are any discrepancies in the email it is a strong sign the email is fraudulent (example bob@microsoft.com vs. bob@micr-soft.com). For any links that are included in the email you can hover your mouse over the link to see the full URL, if the URL is not the same as text it may be a phishing attempt.
How DTonomy Can Help
Of course, these tips are helpful at a small-scale. On a larger scale, DTonomy’s AI-assisted Security Incident Response Platform with Orchestration and Automation can be your long-term solution. With DTonomy, you can:
- Consolidate & manage all alerts
- Automate investigation & response processes using AI
- Cut days of looking at alerts into minutes, or even seconds
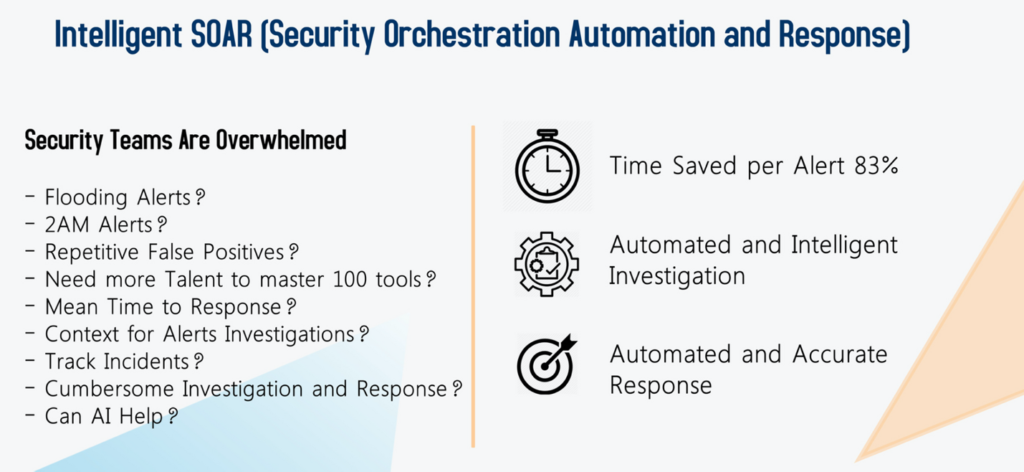
How DTonomy AIR Works
DTonomy AIR (Assisted Incident Response) is an Intelligent Security Orchestration, Automation & Response platform that provides intelligent diagnostics & automated response. Built by Security Analysts for Security Analysts, it is the best assistant you can have as it learns from context continuously & makes smart recommendations that matter most.
- DTonomy consolidates all of your Alerts. (SIEMS/End Point/Email/Network/Vulnerabilities, etc.)
- DTonomy enriches context automatically & identifies patterns intelligently and continuously
- DTonomy connects with your tools & empowers you to build/rescue automated workflows without code.
- DTonomy integrates with 100+ tools and data sources
- DTonomy generates Investigation & Response reports automatically
If you’d like to learn more about DTonomy & how it can help you navigate & protect against ongoing COVID-19 themed cyber attacks, please visit www.dtonomy.com/covid19 or submit this form to request free access to DTonomy tools & services.

