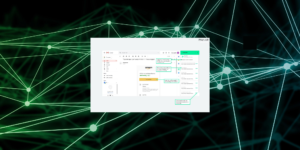
DTonomy’s Free G Suite and Gmail Plugin
As phishing email attacks become more sophisticated and more businesses and educational institutions continue to support remote work options, having a fast phishing alert system is

As phishing email attacks become more sophisticated and more businesses and educational institutions continue to support remote work options, having a fast phishing alert system is

Phishing emails are a type of online scam where criminals send an email that appears to be from a legitimate company and ask you to

Data Loss Prevention (DLP) is both a strategy as well as software products and technologies that are designed to prevent critical information from being leaked

Root Cause Analysis is a Highly Time-Consuming Process Due to the high volume of alerts that security analysts face every day, many alerts are investigated

Managed Detection and Response companies that augment in house security teams with unique skills to improve their threat detection, incident response and monitoring of assets
Running a SOC center with many customers relying on analysts to quickly detect, investigate and resolve security incidents requires the best and most advanced tools

Hackers Increasingly Exploiting Cloud Misconfigurations When Covid-19 exploded on the scene, companies rushed to send employees to work from home. In order to make essential

According to a study last year by Capgemini Research Institute titled Reinventing Cybersecurity with Artificial Intelligence: The New Frontier in Digital Security, they stated that

Fleming Shi, Chief Technology Officer at Barracuda, an email security company, shared highlights from a recent survey that found that almost half (46%) of global

These are highly challenging times in Cyber Security. The volume, complexity and sophistication of threats continues to increase at an alarming and exponential rate. Today,
We are pleased to announce that DTonomy is now part of Stellar Cyber. The integrated solution will enhance cyber threat detection and response automation!