Automate Security Executive Dashboards on Power BI: How to Architect the Data pipeline
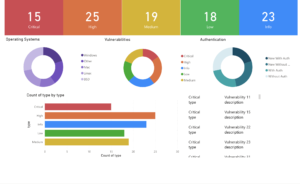
In the backend of security operations, one of the recurring challenges for security teams is automating Power BI dashboards to provide continuous, real-time insights from