Security Information Event Management (SIEM) platforms are an essential part of a modern Security Operations Center (SOC). The SIEM performs the important functions of:
- Collecting and aggregating log data generated across the vast technology infrastructure of an organization
- Identifying, categorizing and analyzing events against carefully designed rules and filters
- Providing reports on security related incidents and events and sending alerts on potential security issues that analysts must take action on
Given that a SIEM processes huge amounts of log data every day, it also generates a large volume of alerts. This overload of alerts that need to be processed can result in ‘alert fatigue’ as humans need to handle a large number of repetitive actions, and many alerts can turn out to be false positives or hard to determine its result given limited information. Security Operation Centers need to focus analysts on the most critical problems and reduce Mean Time to Response (MTTR).
Let’s zoom in the security investigation and response process in SOC center after SIEM alerts are created. The current SOC process can be broken down into five steps.
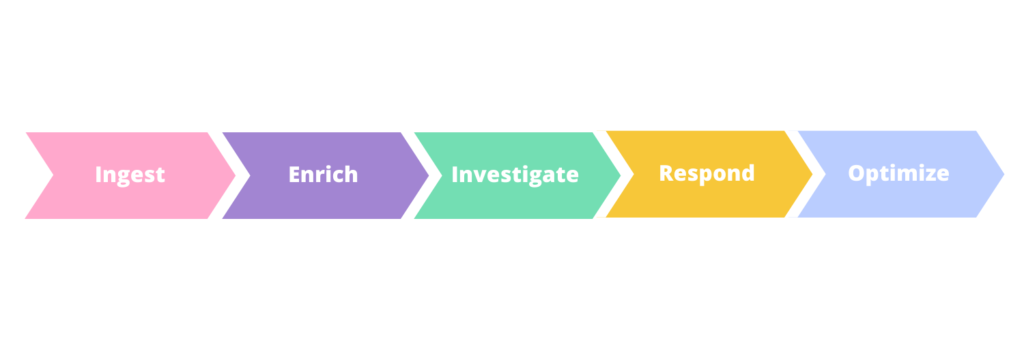
Ingest: consume a large set of alerts from a variety of sources so they can be managed
Enrich: deduplicate alerts and bring extra context from other threat intelligence sources or detections
Investigate: discover patterns and root causes to determine true positives and false positive
Respond: make decisions and take action to stop the attacks and remediate security risk.
Optimize: determine how to improve detection logic and create workflows to eliminate extra manual tasks and improve the efficiency of SOC center
How can DTonomy augment SIEM and SOC processes to address alert fatigue?
DTonomy AIR can further augment your SIEM and SOC processes to eliminate alert fatigue and improve the efficiency of your SOC on top of each step discussed above.
Intelligent Deduplication – in the enrich phase, DTonomy AIR automatically analyzes data over desired time frames and consolidates all duplicate alerts together
Intelligent Pattern Discovery – in the investigation phase, DTonomy AIR employs a variety of different algorithms designed by data scientists and security experts and continuously extracts patterns in alerts and provides other not obvious insights that would otherwise cause analysts to run endless queries. Algorithm driven, no need to manage complicated rules.
Guided Response – in the response phase, DTonomy AIR leverages the collective knowledge of analysts, crowdsourced intelligence and built-in playbooks to provide accurate recommendations for handling security alerts personalized to your environment.
Continuous Process Automation – in the optimize phase, as DTonomy AIR becomes smarter over time, it learns from actions being taken and makes adaptive recommendations on how to refine logic for detection, adds appropriate filters for handling false positives, and monitors the efficiency of the playbooks.
Automated Enrichment – in the enrich phase, DTonomy AIR enables you to automate the customized correlation between your detections and other threat intelligence or detections so that you can view them in one place without navigating through pages after pages.
Automated Response Actions – in the response phase, DTonomy AIR is able to automate responses using built-in playbooks. DTonomy AIR integrates with hundreds of popular security tools including open source and enterprise.
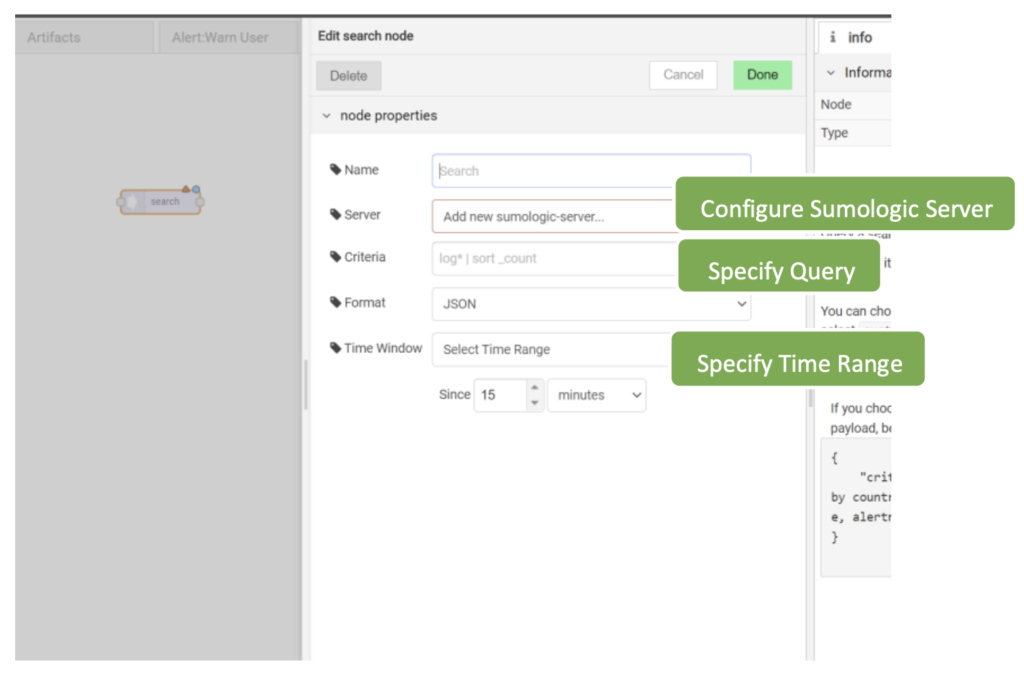
DTonomy AIR is integrated with multiple SIEM products including but not limited to SumoLogic, Elastic Search, Exabeam, Wazuh, and Splunk. (Our full list of integrations can be seen here) As an example, our Sumologic integration enables you to easily ingest alerts:
Use DTonomy AIR to augment your SIEM for efficient security response – reducing alert fatigue, Mean Time to Response and mitigating security risk. Request a demo today!

