Automate Threat Hunting Across All Your Datasets
THE CHALLENGE:
Threat hunting is time-consuming especially when you do not have or afford centralized data storage for all your data sets. The security teams have to go through different platforms to find relevant data and build a convincing story.
THE SOLUTION:
DTonomy’s automation platform made it easy for security analysts to conduct threat hunting on soiled data sets across all the IT systems including both on-premise and in the cloud. Save time on opening multiple applications and copy-paste results here and there. Instead, see threat hunting results in one place.
How? Through No-Code Automation Platform.
Here is an example:
- Analysts query crowd strike to find affected machines
- Based on affected machines, analysts query Rapid 7 to see how many of them have critical vulnerabilities
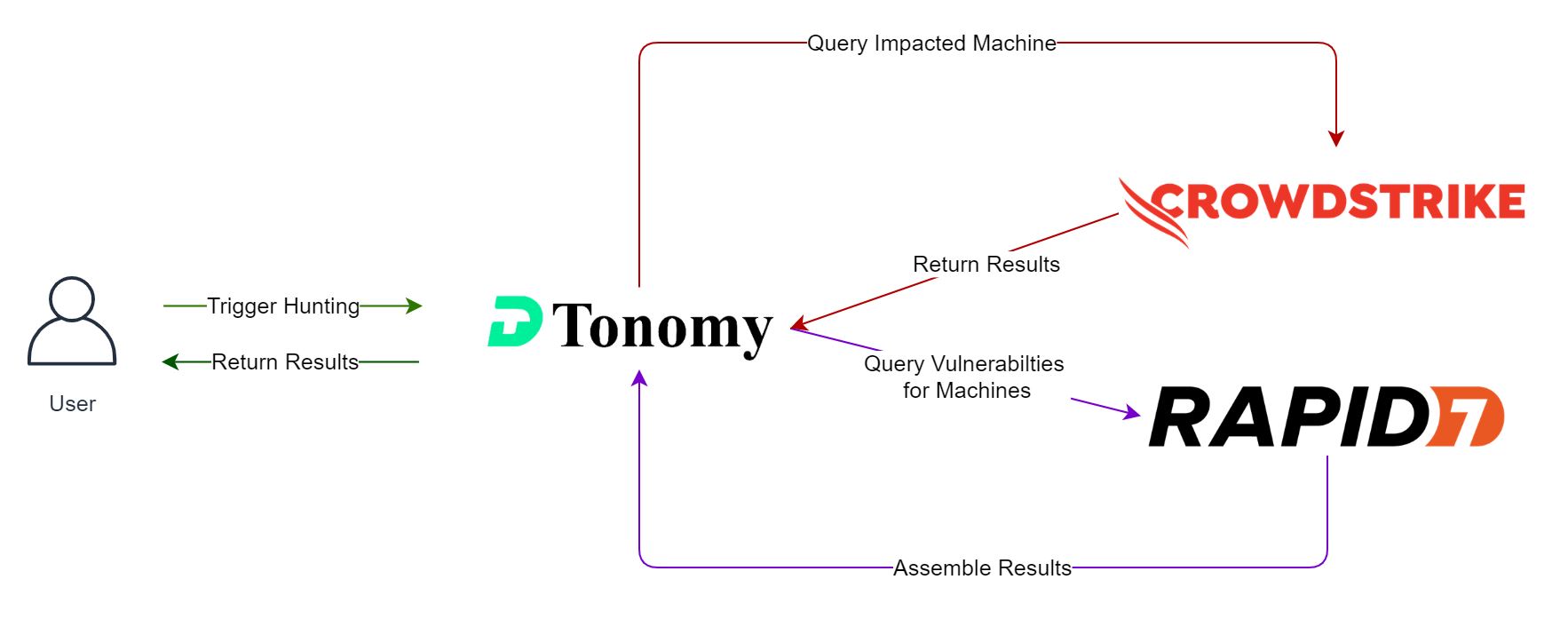
With DTonomy, you can trigger consecutive queries automatically from one place automatically or repetitively. DTonomy reaches out to each application, collects results, and assembles results as well for you to review. So you do not need to
- Open many applications
- Copy-paste results
- Store your threat hunting processes in random places
- Worry about missing information
Are you ready to automate SOC activities?

Copyright © DTonomy 2022
Consolidate Siloed Security Insights