Security Orchestration, Automation and Response
THE CHALLENGE:
Security teams face the challenge of lacking resources to effectively battle threats from various sources such as cloud environments, endpoints, networks, and email. While automation is useful for saving time, increasing analyst efficiency, and expanding threat coverage, it can be time-consuming to create and maintain.
THE SOLUTION: Managed SOC Automation Services
Our managed SOC automation service, powered by DTonomy’s SOAR platform, addresses these challenges by managing and maintaining automation for you.
With hundreds of built-in integrations, DTonomy enables security analysts to orchestrate and automate siloed security tools from a single platform. SOC teams can automate security operations such as security control validation, cloud security response, and phishing email analysis. DTonomy’s AI-based analysis and response capabilities help unlock more security automation, orchestrate SOC tools, maximize the ROI of existing security investments, and reduce risks.
You tell us what you need, and we deliver and maintain the automation service for you.
Limitless Use Cases
Security Control Validation
Quickly implement automation to ensure security controls are regularly validated. For example, ensure your DLP configuration works as expected all the time.
Automate Threat and Context Enrichment
Add rich threat intelligence resources and local topology information to provide context for alert investigations with simple no-code automation.
Incident Response Automation
Hundreds of playbooks with automated best practice recommendations in context, automate actions like blocking IPs, quarantining machines, sending notifications, etc.
Threat Hunting Automation
Schedule your favorite threat-hunting tasks continuously and easily by leveraging flexible data source integrations.
Attack Surface Management
Make sure blind or weak spots on internet-facing assets are addressed timely with DTonomy as soon as they are discovered.
Siloed Data Consolidation
Create centralized security metrics using popular BI tools or conduct live queries without the need to store your data in one place.
Cloud Compliance Automation
Continuously monitor cloud artifacts such as users and machines to ensure they meet compliance requirements.
Cloud Security Posture Remediation
Monitor changes and configuration in your cloud environment and ensure cloud misconfiguration is handled immediately by the right person with automation in place.
Orchestrate Human & Machine
Orchestrate machine automation and human tasks seamlessly with built-in mechanisms that enable continuity of automation conditioned upon certain human actions.
Eliminate Security Alert Fatigue
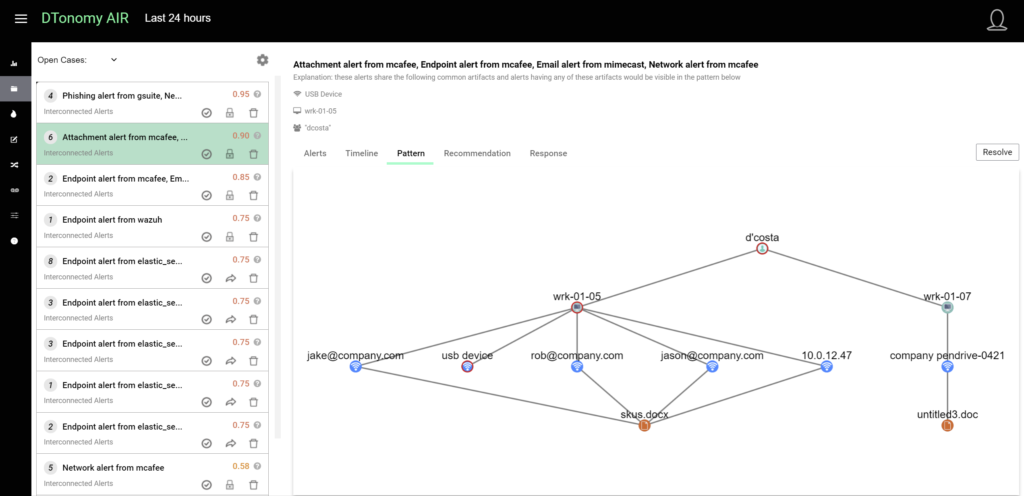
DTonomy’s AI-based cross-correlation and adaptive learning capabilities don’t only look for anomalies, instead, it looks for relationships between alerts. Too often atomic alerts are too noisy and not practical to start an investigation without proper correlation. Writing correlation rules manually is a time-consuming, never-ending task and limits the possibility of discovering new types of attacks. Additionally, as analysts triage security alerts, the analyst’s knowledge and processes are not captured, slowing down future resolution activities. When security teams can correlate alerts and capture previous response activities, teams can use pattern analytics to enable you to triage security alerts much more efficiently. The DTonomy system ‘learns out’ false positive patterns based on security analysts’ activities. Doing this provides analysts with a smaller number of automatically-grouped alerts to review more efficiently.
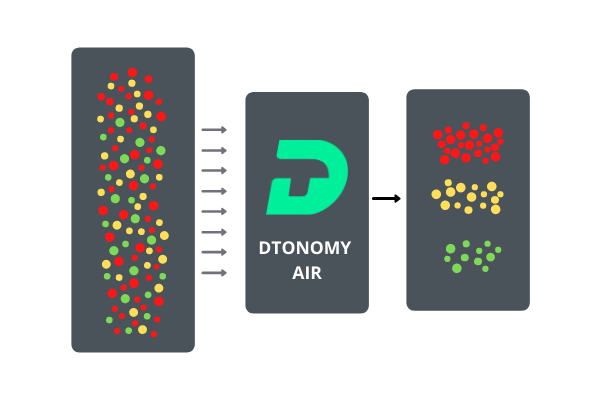
Using a pattern-driven approach, true positives can be viewed quickly as being aligned with attack processes such as MITRE ATT&CK framework. Likewise, there are patterns exhibited by false positives as well. For example, if you see multiple machines connecting to a single IP generating 100 alerts at the same time frame, or always aligning with certain deployment activity, that will give you confidence that they are false positives. DTonomy learns these patterns, enriches context for the alerts, ultimately helping to automatically identify both true positive and false positive much faster.
DTonomy uses AI algorithms to discover patterns that augment your manual correlation process
 Trustworthy AI is used to ensure you are leveraging the power of AI confidently.
Trustworthy AI is used to ensure you are leveraging the power of AI confidently.
The DTonomy pattern-driven approach enables SOC teams to:
- Deduplicate alerts so that repetitive alerts are easily tracked and teams do not waste time triaging similar alerts again and again
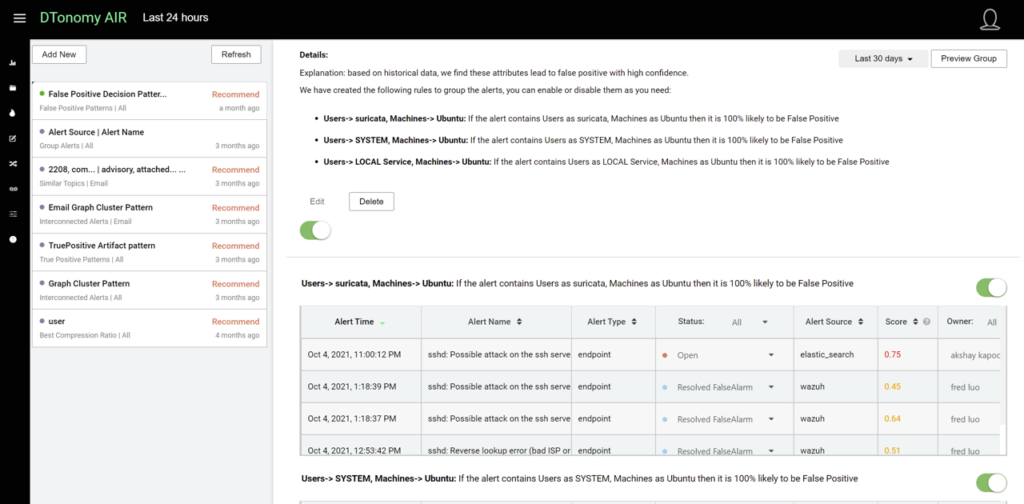
- Identify false positive patterns based on learning from analysts’ resolutions that are applied to help quickly identify similar future alerts
- Automatically personalize security risk scores based on previous analyst resolutions that DTonomy has learned
- Recommend appropriate playbook response based on the alert type and historic resolution activities
- Enable you to unlock more automation that suits your environment
- Keep the SOC optimized automatically and continuously
Are you ready to speed up security investigation?
Try it out!

Copyright © DTonomy 2024